Malspam pushing Locky ransomware tries HoeflerText notifications for Chrome and FireFox
2017-09-01 update: A different campaign using HoeflerText popups has been active during the same timeframe. I wrote about it here, but the only thing these two campaigns have in common is that they both used HoeflerText popups.
Introduction
During past two weeks or so, we've seen plenty of botnet-based malicious spam (malspam) pushing Locky ransomware. In recent days, I've noticed multiple waves of malspam every weekday. It gets a bit boring after a while, but as 2017-08-31 came to a close, I noticed a different technique from this malspam.
Today's malspam had links to fake Dropbox pages. If you viewed the pages in Chrome or Firefox, they showed a fake notification stating you don't have the HoeflerText font. These fake notifications had an "update" button that returned a malicious JavaScript (.js) file. These .js files were disguised as a font library.
Of note, I was unable to get any malware when using Internet Explorer or Microsoft Edge.
The emails
The emails were botnet-based, and they came from various IP addresses around the world. The message-ID header was spoofed, so that it ended with @us-west-2.amazonses.com>. However, the few emails I examined closely didn't come from Amazon servers. Email headers follow:
- Date/Time start: Thursday 2017-08-31 as early as 23:50 UTC
- Date/Time finish: Friday 2017-09-01 as late as 01:41 UTC
- Sender (spoofed): "Dropbox" <no-reply@dropbox.com>
- Subject: Please verify your email address
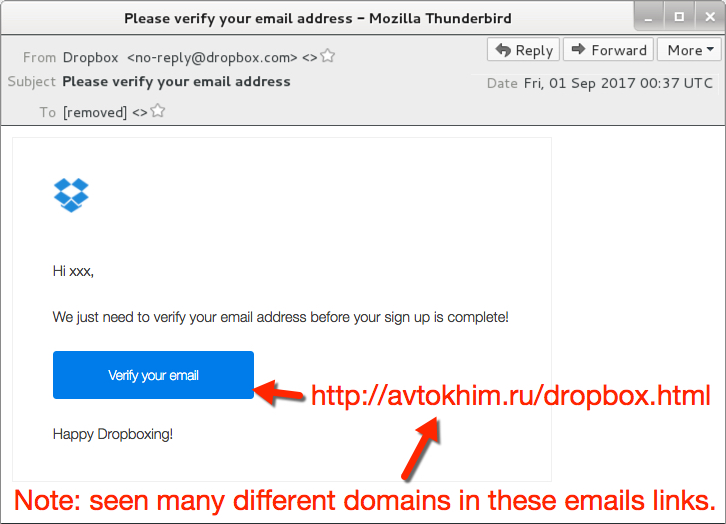
Shown above: Screen shot from one of the emails.
Fake Dropbox sites and HoeflerText notifications
Each link from the malspam went to compromised sites hosting fake Dropbox pages. When I viewed the links in Internet Explorer 11 or Microsoft Edge, they merely showed a fake Dropbox page. I believe they should've returned something after I clicked a link in "Please click here to download a new verification message." But that didn't work for me.
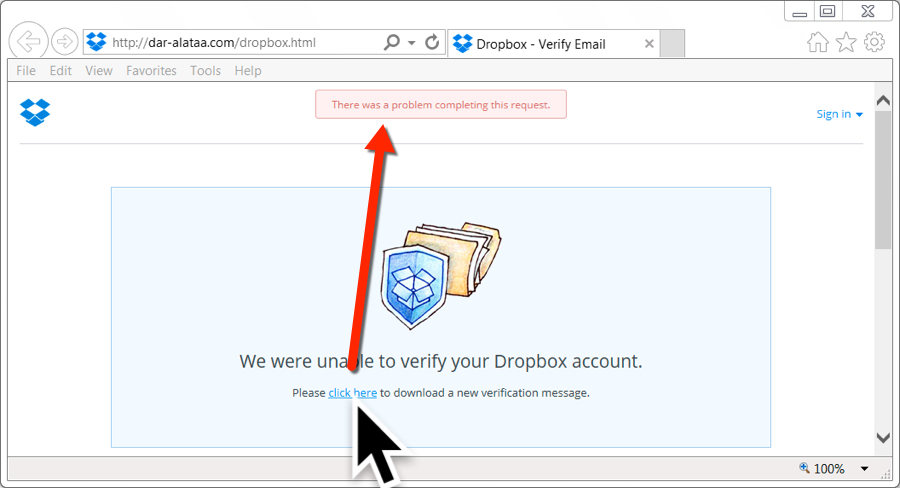
Shown above: Bogus site, but nothing when I tried it in IE or Edge.
However, when I tried these same links in Google Chrome, they displayed a fake notification stating: The "HoeflerText" font was not found. These notifications also had an "update" button. When I clicked it, I received a JavaScript file named Win.JSFontlib09.js. That JavaScript file is designed to download and install Locky ransomware.
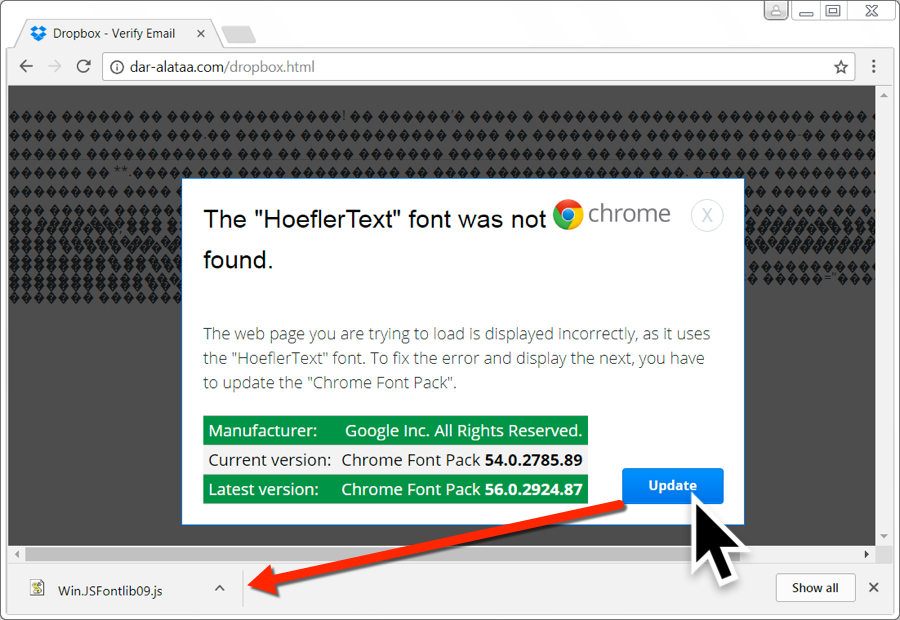
Shown above: Bogus site with a HoeflerText popup when viewing it in Chrome.
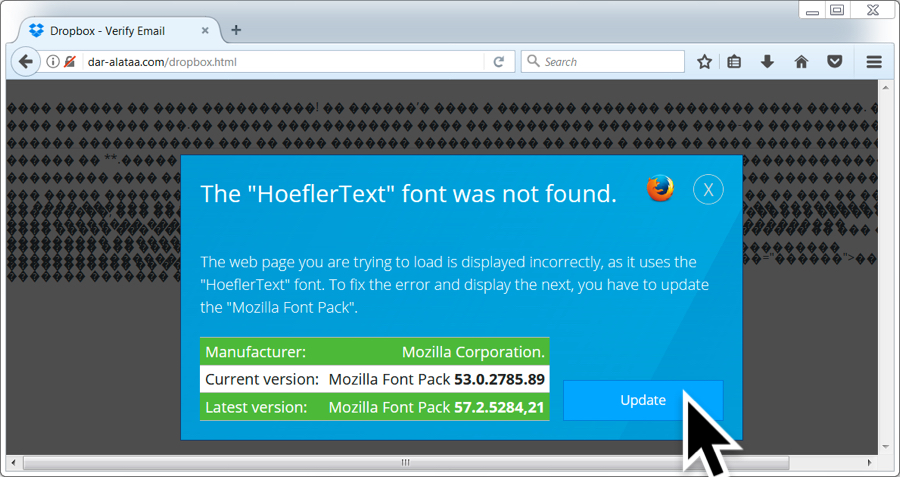
Shown above: Bogus site with a HoeflerText popup when viewing it in FireFox.
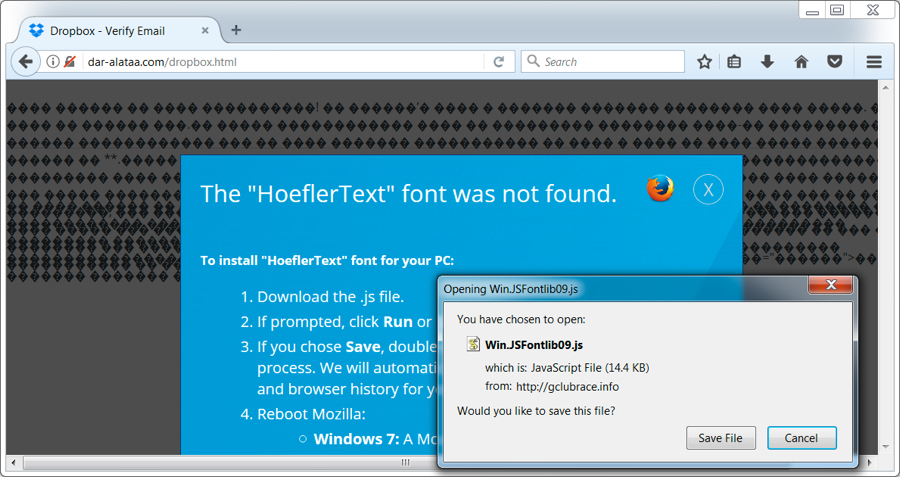
Shown above: Bogus site with a HoeflerText popup when viewing it in FireFox after clicking "update".
I tried different browsers and had mixed results. Tor and Yandex browsers both returned the same results as IE 11 and Microsoft Edge when viewing those fake Dropbox pages. Opera and Vivaldi returned the same HoeflerText notifications seen in Google Chrome.
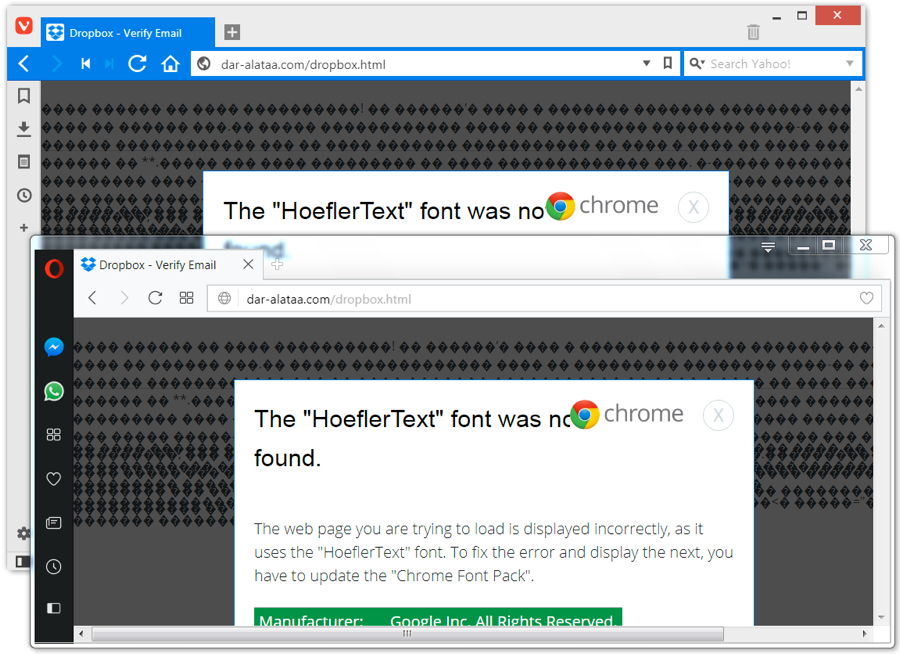
Shown above: Bogus site in Opera or Vivaldi gave the Chrome notification.
Win.JSFontlib09.js was similar to what we've seen in recent weeks for JavaScript downloaders that retrieve Locky ransomware.
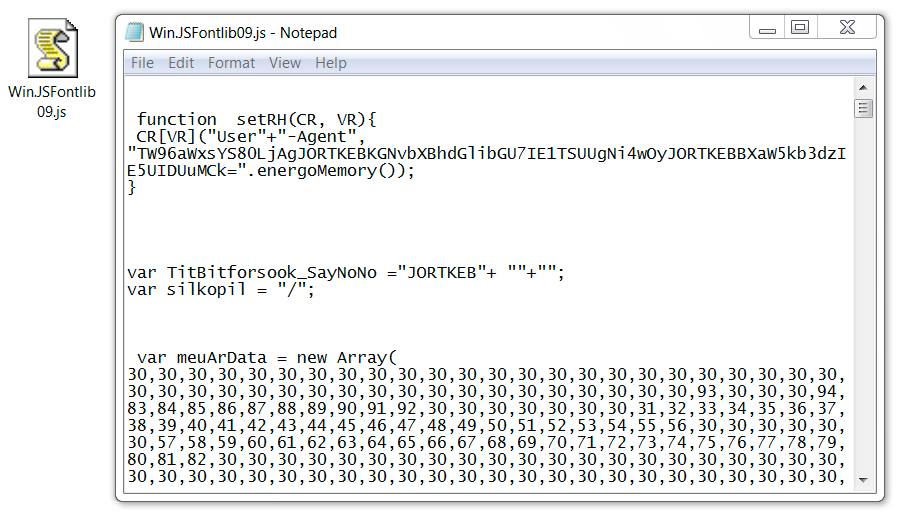
Shown above: Win.JSFontlib09.js from the fake HoeflerText notifications.
Network traffic
Network traffic wasn't too terribly different than what we've seen with other Locky infections. It just had an added step with the HoeflerText popup. The image below explains the network traffic from an infection in one of my lab hosts.
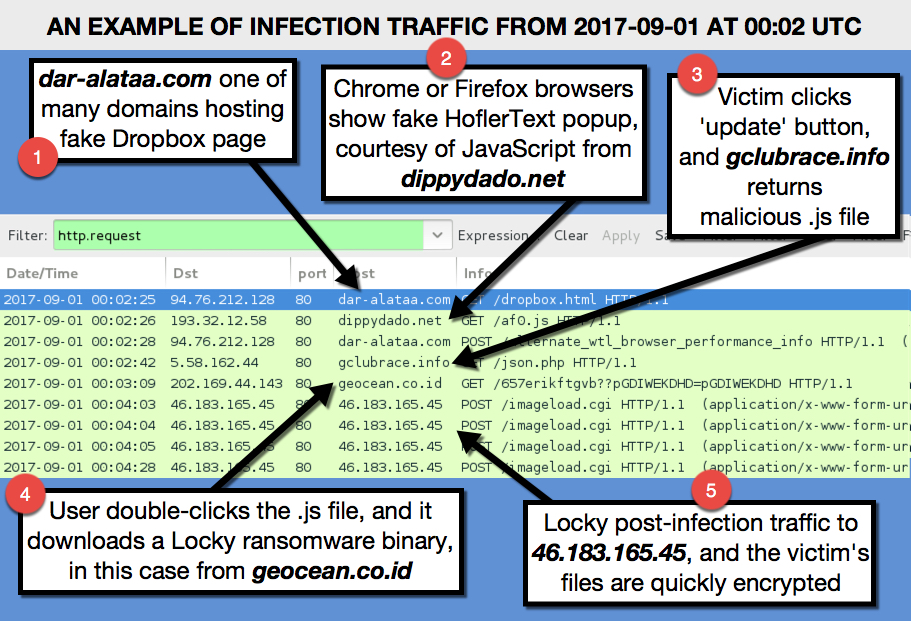
Shown above: Traffic from an infection filtered in Wireshark.
Indicators
The following are URLs I found from the malspam. They're "de-fanged" so you can't accidentally click on them and go to the fake Dropbox pages.
- hxxp://albion-cx22.co[.]uk/dropbox.html
- hxxp://ambrogiauto[.]com/dropbox.html
- hxxp://arthurdenniswilliams[.]com/dropbox.html
- hxxp://autoecoleathena[.]com/dropbox.html
- hxxp://autoecoleboisdesroches[.]com/dropbox.html
- hxxp://autoecoledufrene[.]com/dropbox.html
- hxxp://avtokhim[.]ru/dropbox.html
- hxxp://bayimpex[.]be/dropbox.html
- hxxp://binarycousins[.]com/dropbox.html
- hxxp://charleskeener[.]com/dropbox.html
- hxxp://campusvoltaire[.]com/dropbox.html
- hxxp://dar-alataa[.]com/dropbox.html
- hxxp://flooringforyou.co[.]uk/dropbox.html
- hxxp://gestionale-orbit[.]it/dropbox.html
- hxxp://griffithphoto[.]com/dropbox.html
- hxxp://jakuboweb[.]com/dropbox.html
- hxxp://jaysonmorrison[.]com/dropbox.html
- hxxp://patrickreeves[.]com/dropbox.html
- hxxp://potamitis[.]gr/dropbox.html
- hxxp://tasgetiren[.]com/dropbox.html
- hxxp://willemshoeck[.]nl/dropbox.html
URL that returned script causing HoeflerText popups in Chrome (and Firefox):
- hxxp://dippydado[.]net/af0.js
URL that should've returned some sort of malware when viewing the fake Dropbox sites in IE or Edge (but did not work):
- hxxp://dippydado[.]net/json.php
URL that returned Win.JSFontlib09.js after clicking 'update' on the HoeflerText popup:
- hxxp://gclubrace[.]info/json.php
URL to retrieve the Locky binary after double-clicking Win.JSFontlib09.js:
- hxxp://geocean.co[.]id/657erikftgvb??pGDIWEKDHD=pGDIWEKDHD
Locky ransomware post-infection URL:
- http://46.183.165.45/imageload.cgi
SHA256 hash for Win.JSFontlib09.js:
SHA256 hash for the Locky binary:
Final words
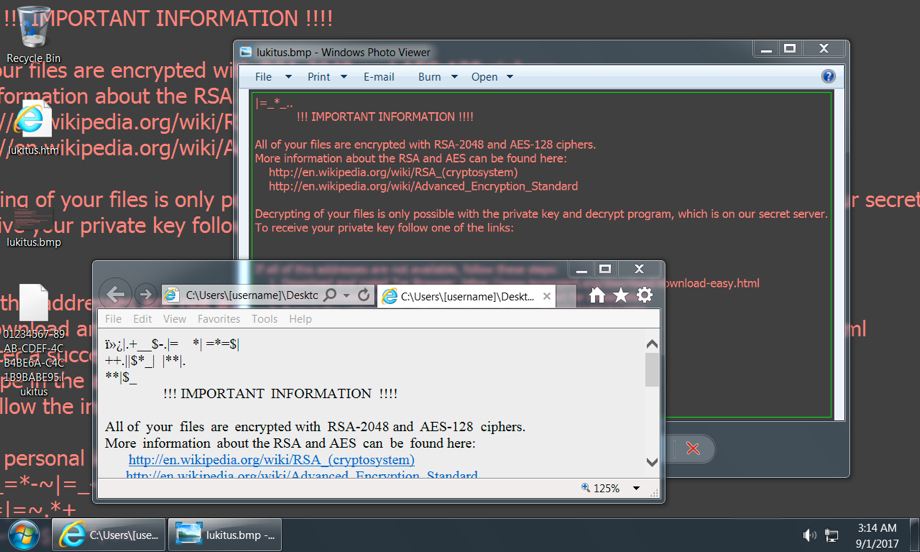
Shown above: Desktop of an infected Windows host from my lab.
Ultimately, this infection wasn't very innovative. The ransomware was the "Lukitus" variant of Locky, which has been out for a while, and it's easily detectable. We've seen all the individual techniques used during the entire infection chain. However, it cobbled together some existing tricks like HoeflerText popups with fake Dropbox pages, so it briefly excited me as I looked into it.
As always there are plenty of good practices that users and administrators can follow to avoid getting infected by this malware.
A pcap of the network traffic can be found here. It's password protected with the standard password. If you don't know it, look at the "about" page of my blog at malware-traffic-analysis.net.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments