Windows SMBv3 Denial of Service Proof of Concept (0 Day Exploit)
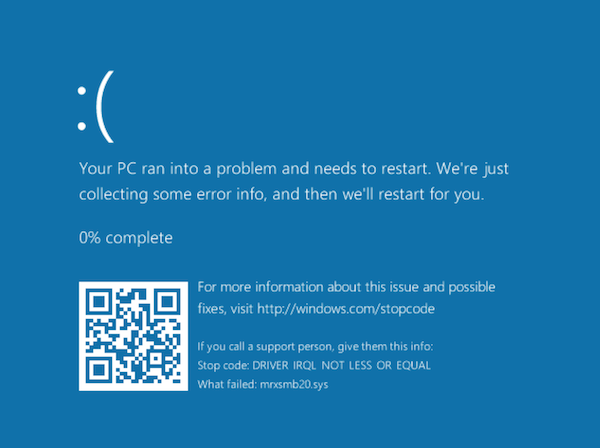
The tweet originally announcing this issue stated that Windows 2012 and 2016 is vulnerable. I tested it with a fully patched Windows 10, and got an immediate blue screen of death (see below for screenshot).
A "Proof of Concept" (PoC) Exploit causing a blue screen of death on recent Windows version was released on Github earlier today. The exploit implements an SMBv3 server, and clients connecting to it will be affected. An attacker would have to trick the client to connect to this server. It isn't clear if this is exploitable beyond a denial of service. To be vulnerable, a client needs to support SMBv3, which was introduced in Windows 8 for clients and Windows 2012 on servers.
Right now, I do not see a Microsoft statement regarding this exploit and the vulnerability triggered by it. Of course, it is best practice to block port 445 inbound AND outbound on your firewall, limiting the impact somewhat.
A traffic capture I collected between two virtual machines (Windows 10 victim) can be found here: https://isc.sans.edu/diaryimages/smbexploit.pcap . The exploit can be seen in packet 27 and 28. The long string of "C"s does trigger the buffer overflow.
After the (normal) "Tree Connect Request" message, the server responds with a crafted "Tree Connect Response" message. The message itself is actually kind of ok, but the length of the message is excessive (1580 Bytes) and includes a long trailer.
The tree connect response message consists of:
- NetBIOS header. This just includes the message type (0) and the total length (1580 in this case).
- SMB2 header: The usual 64 bytes. The "Command" indicates that this is a tree connect message and the response flag is set.
- The Three Connect Response Message. This message has a fixed length of 8 bytes in addition to the fixed header.
This is where the message should end. But apparently, since the total message size according to the NetBIOS header is larger, Windows keeps on decoding in the crafted header (all "C"s in the exploit) which then triggers the buffer overflow.
Based on this understanding of the exploit (please let me know if I didn't get it right or missed something), I wrote a simple snort signature that looks for Tree Connect messages that exceed 1000 bytes in size. Use this at your own risk. It is in "works for me" state:
alert tcp $EXTERNAL_NET 445 -> $HOME_NET any (sid: 10001515; msg: "SMB Excessive Large Tree Connect Response"; byte_test: 3,>,1000,1; content: "|fe 53 4d 42 40 00|"; offset: 4; depth: 6; content: "|03 00|"; offset: 16; depth:2 ;)
The exploit can be found here: https://github.com/lgandx
Blue Screen of death after successful exploit:
Multiple vulnerabilities discovered in popular printer models
Researchers from University Alliance Ruhr have announced that they have discovered vulnerabilities in popular laser printers including models from HP, Lexmark, Dell, Brother, Konica and Samsung. The announced vulnerabilities have a range of effects, but could permit the contents of print jobs to be captured, permit delivery of buffer overflow exploits, password disclosure or even damage to the printer.
The vulnerabilities are in PostScript and Printer Job Language (PJL) and have been around for decades, exploiting limitations of the languages used by most printers. The vulnerabilities can definitely be exploited from the local network, but it is possible that a malicious website could also use cross-site scripting to exploit the vulnerabilities.
It is estimated that up to 60,000 currently deployed printers may be vulnerable.
More information on the research can be found at hacking-printers.net
The researchers have also developed and set of tools called the Printer Exploitation Toolkit (PRET) which can be used to launch the attacks against these vulnerabilities.
The vulnerability disclosures are:
PostScript printers vulnerable to print job capture
Various HP/OKI/Konica printers file/password disclosure via PostScript/PJL
HP printers restoring factory defaults through PML commands
Multiple vendors buffer overflow in LPD daemon and PJL interpreter
Brother printers vulnerable to memory access via PJL commands
Multiple vendors physical NVRAM damage via PJL commands
I am still digging, but so far I have not been able to find any vendor responses to these vulnerability advisories. If you see any please comment on this diary or through our contact page.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)


Comments