VBA Shellcode and EMET
Someone asked me if EMET would stop the malicious document I analyzed in my diary entry Hancitor Maldoc Bypasses Application Whitelisting.
In its default configuration, EMET will stop the shellcode from executing inside the Word process with its EAF protection. But there is no specific mitigation for the process replacement/process hollowing attack.
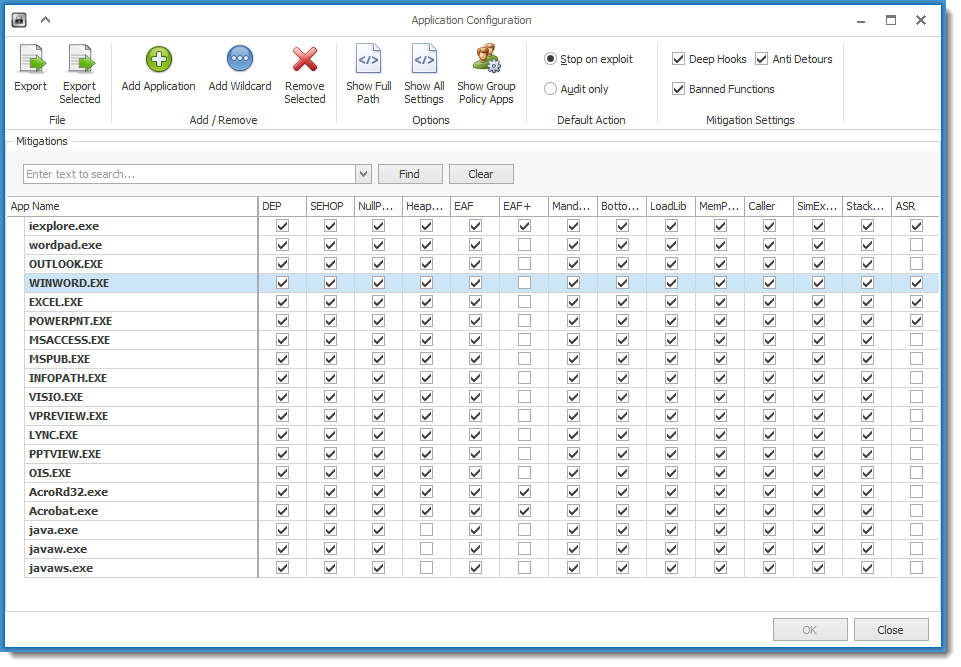
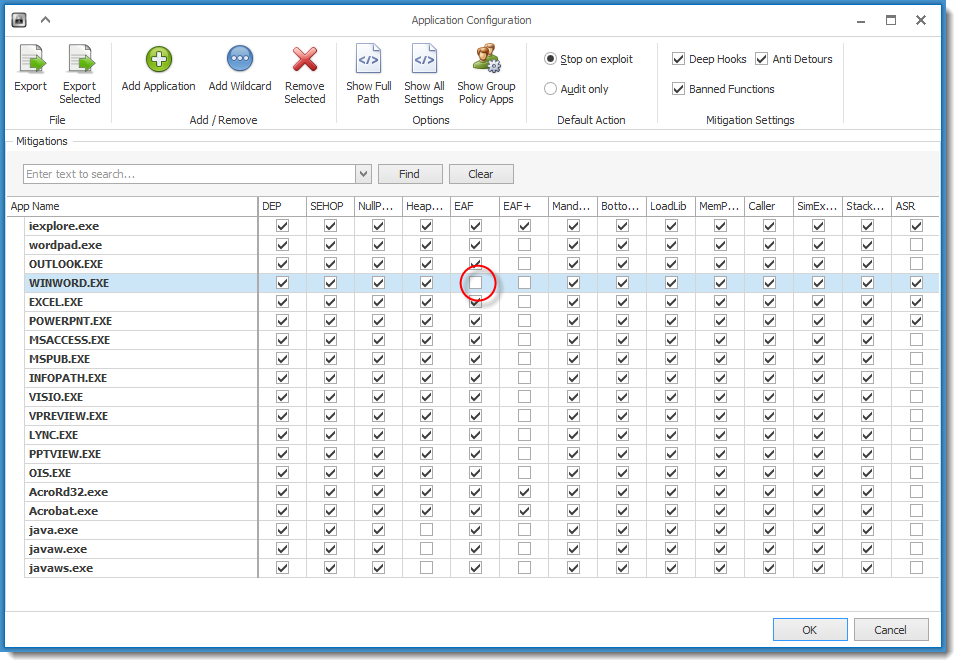
By default, EMET protects MS Word:
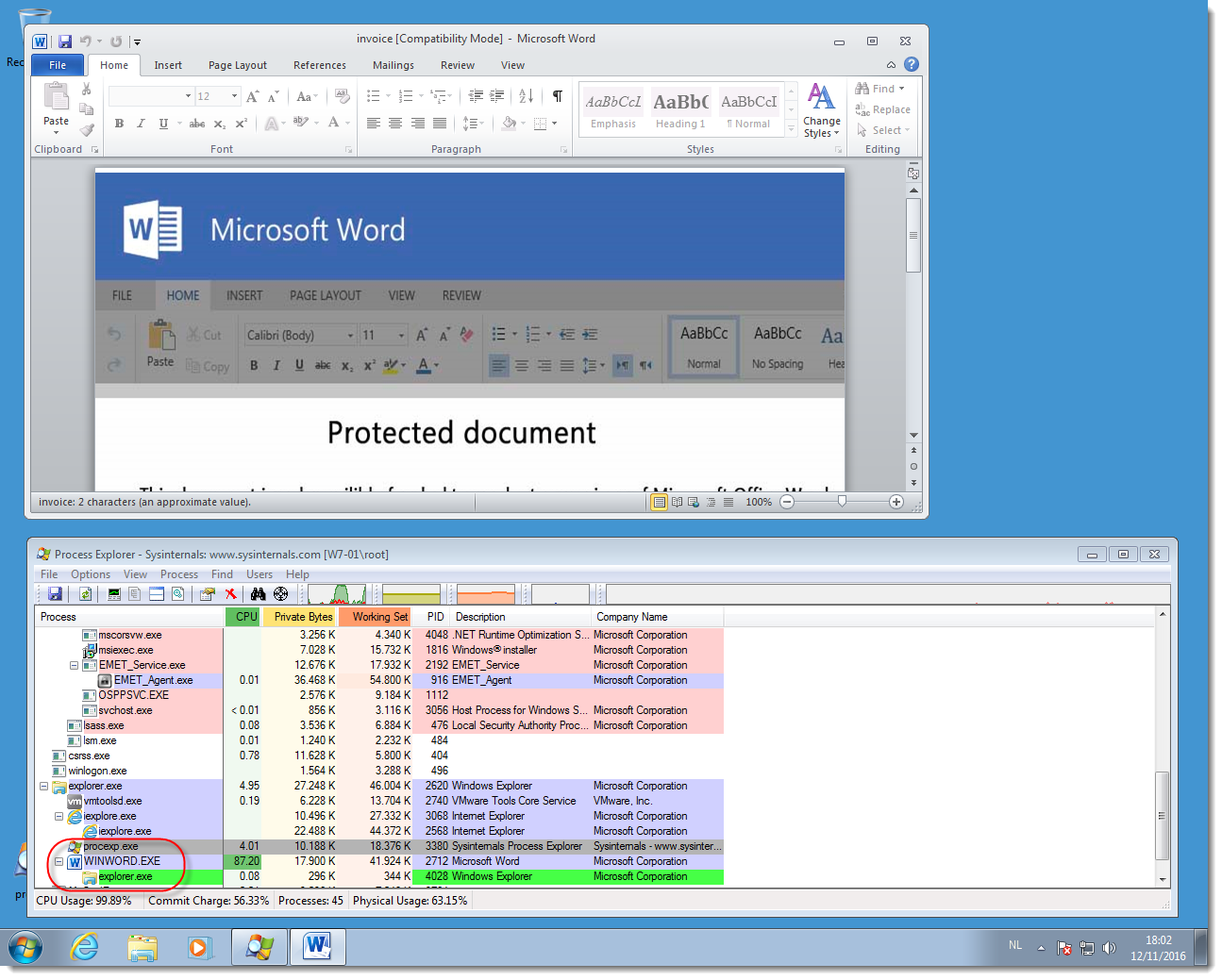
Opening the malicious Word document:
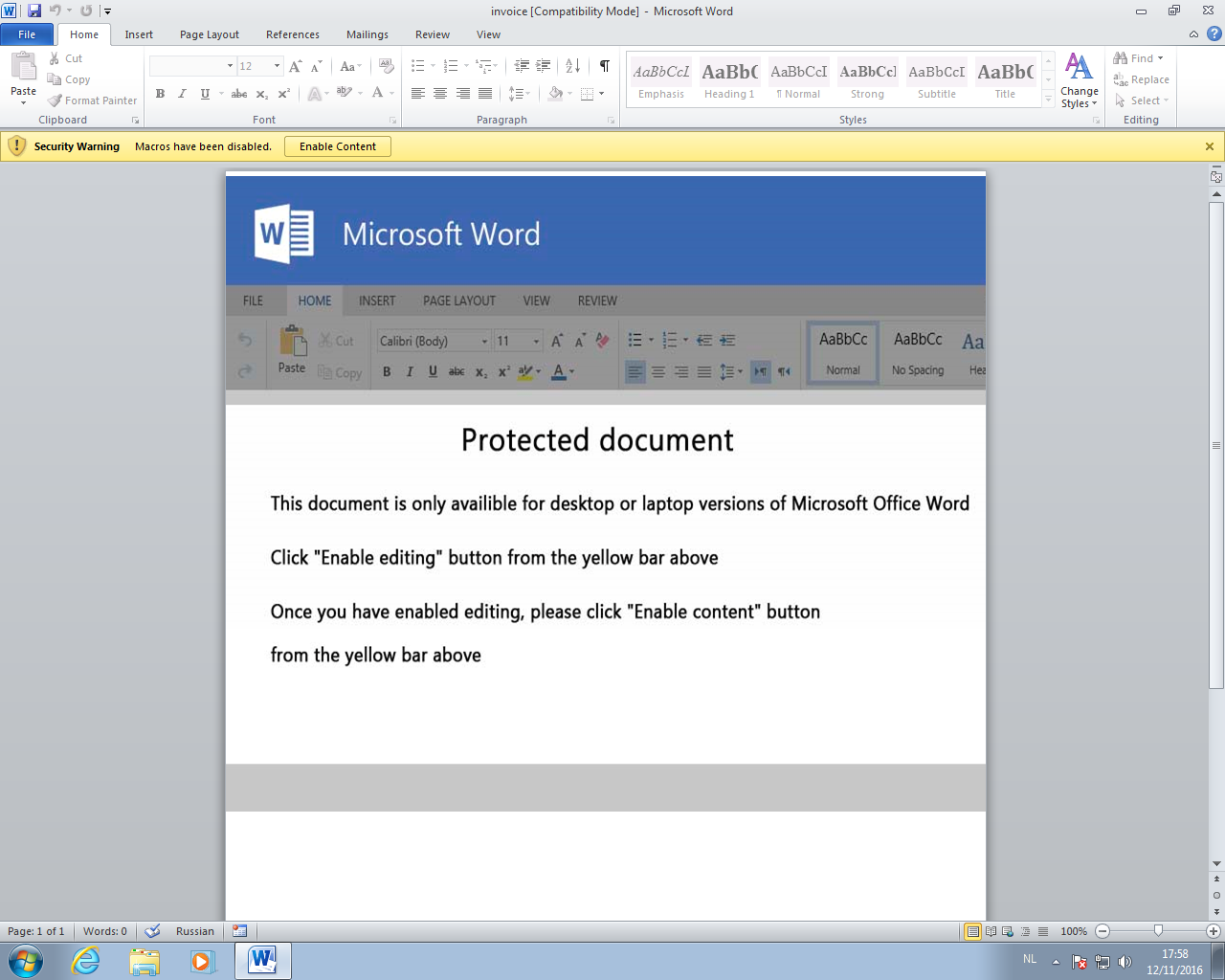
Because of the default macro settings, the VBA code will not execute.
But when we click Enable Content, the VBA code will execute. It will inject shellcode inside the Word process, and this shellcode will lookup the API functions it needs. This behavior will be detected by EMET's Export address table Access Filtering (EAF) and the Word process will be killed.
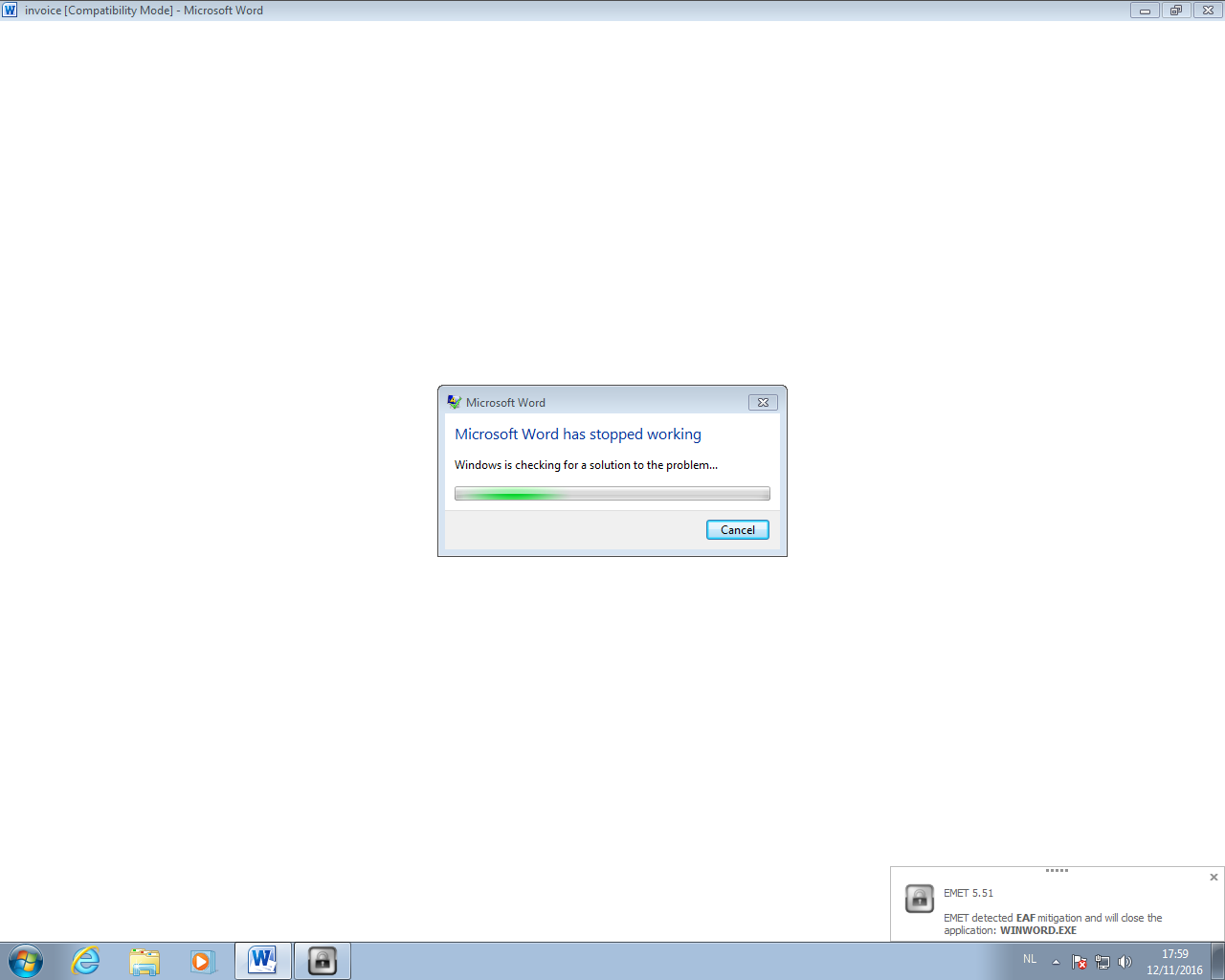
When we disable EAF, the shellcode will be able to run and thus do the process replacement. There is no mitigation for process replacement.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
NVISO


Comments