Massive malware spam campain to corporate domains in Colombia
Published: 2015-05-01. Last Updated: 2015-05-01 18:46:28 UTC
by Manuel Humberto Santander Pelaez (Version: 1)
6 comment(s)
by Manuel Humberto Santander Pelaez (Version: 1)
There was a massive malware spam campain directed to corporate domains in Colombia. The following was the e-mail received:
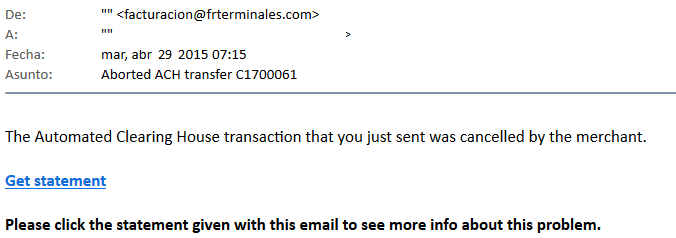
Now this e-mail has two interesting aspects:
- It is tracking if the user reads the message using the google analytics API by invoking the following:
img src=3Dhttp://www.google-analytics.com/c= ollect?v=3D1&tid=3DUA-62115737-1&cid=3Dxx@xx.com&t=3De= vent&ec=3Dxx@xx.com&ea=3Dopens&el=3Dxx@xx.com&cs=3Dnewsletter&cm=3Demail&cn=3D062413&cm1=3D1?/
- It has a link to a dropbox file being masqueraded with the google url redirection script:
https://www.google.com/url?q=3Dhttps%3A%2F%= 2Fwww.dropbox.com%2Fs%2Fvs5hho625v7ibw5%2FACH=5Ftransaction5721.doc%3Fdl%3D= 1&sa=3DD&sntz=3D1&usg=3DAFQjCNFADf1fsGqdWqwSOnMC6XyLMHrL2w
When opened, this document has embedded a visual basic script that downloads a known trojan password stealer designed for colombian banks.
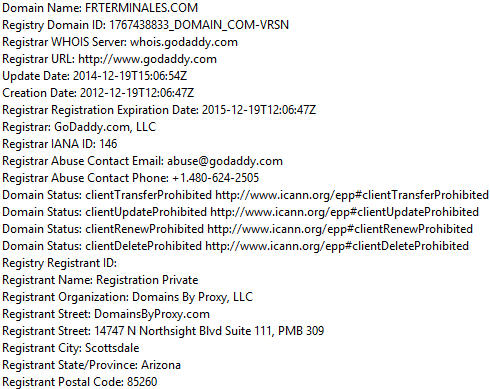
This domain uses a private registation service, avoiding to know the identity of the registrar:
Be careful when opening unknown e-mails. You could be leaking information and compromising your computer, even when you see google domain in the URLs.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
Keywords:
6 comment(s)ISC StormCast for Friday, May 1st 2015 http://isc.sans.edu/podcastdetail.html?id=4465
×
![modal content]()
Diary Archives


Comments