Automating Incident data collection with Python
One of my favorite Python modules is Impacket by the guys at Core Labs. Among other things it allows me to create Python scripts that can speak to Windows computers over SMB. I can use it to map network drives, kill processes on a remote machine and much more. During an incident having the ability to reach out to all the machines in your environment to list or kill processes is very useful. Python and Impacket make this very easy. Check it out.
After installing Impacket all of the awesome modules are available for use in your Python scripts. In addition to the modules, Impacket also includes several sample programs. Awesome tools like psexec.py gives you functionality like Microsoft's PSEXEC plus pass-the-hash in an easily automated format. Have you ever wished you could run wmic commands from linux? Let use wmiexec.py to run a command on a remote windows machine from Linux. You just provide the tools with a username, password, Target IP address and a wmic command to run on the target machine. For example, this is how to get a list of the users on a remote target.
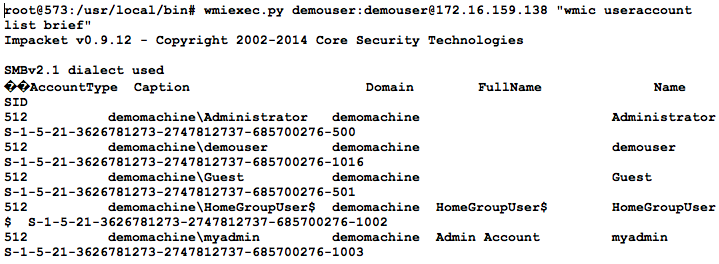
WMIC from my linux server is awesome, but the best part is that this is Python!. So instead of running wmiexec.py I can import it as a module and use in a python script. I'll start out in the same directory as wmiexec and launch "python". Then "import wmiexec" and create a variable to hold a WMIEXEC object. In this case I'll create a variable called wmiobj that points to a WMIEXEC object. The first argument is the command I want to run. In this case I run a WMIC command that will that finds the path of the executable for every copy of a process with "cmd" somewhere in the process name. The only other arguments are the username, password and "share='ADMIN$'".
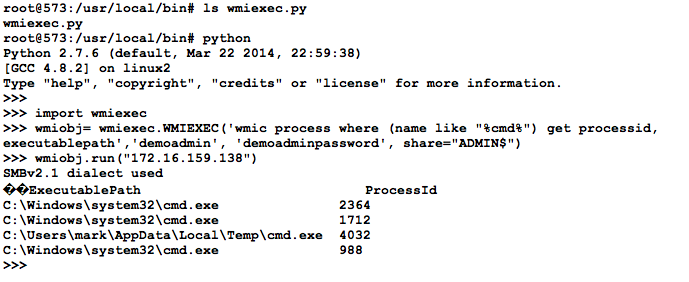
In this case one of the command prompts is running from a users temporary directory. That merits some additional investigation! With those 3 simple lines of Python code we were able to automate the query to a single host. Because it is Python we can easily use a "for loop" to run this on every workstation on our network, capture those result and compare them. Find the host with processes that aren't running on any of the the other hosts! Find the host with unique unusual network connections! Then, if the conditions are right, automate something to isolate it.
Interested in learning more? Come check out SEC573 Python for Penetration Testers. You will learn Python starting from ground zero and learn how to "automate all the things". Join me at Cyber Guardian on March 2 or in Orlando on April 11.
Check out the courses here:
http://www.sans.org/course/python-for-pen-testers
Mark Baggett
twitter:@MarkBaggett


Comments