Heartbleed CRL Activity Spike Found
Update: CloudFlare posted in their blog twice today claiming responsibility for the majority of this spike. Quoting: "If you assume that the global average price for bandwidth is around $10/Mbps, just supporting the traffic to deliver the CRL would have added $400,000USD to Globalsign's monthly bandwidth bill."
Update: We've also seen articles from ZDNet and WIRED today in response to the below insights, with further analysis therein.
It looks like, as I had suspected, the CRL activity numbers we have been seeing did not reflect the real volume caused by the OpenSSL Heartbleed bug.
This evening I noticed a massive spike in the amount of revocations being reported by this CRL: http://crl.globalsign.com/gs/gsorganizationvalg2.crl
The spike is so large that we initially thought it was a mistake, but we have since confirmed that it's real! We're talking about over 50,000 unique revocations from a single CRL:
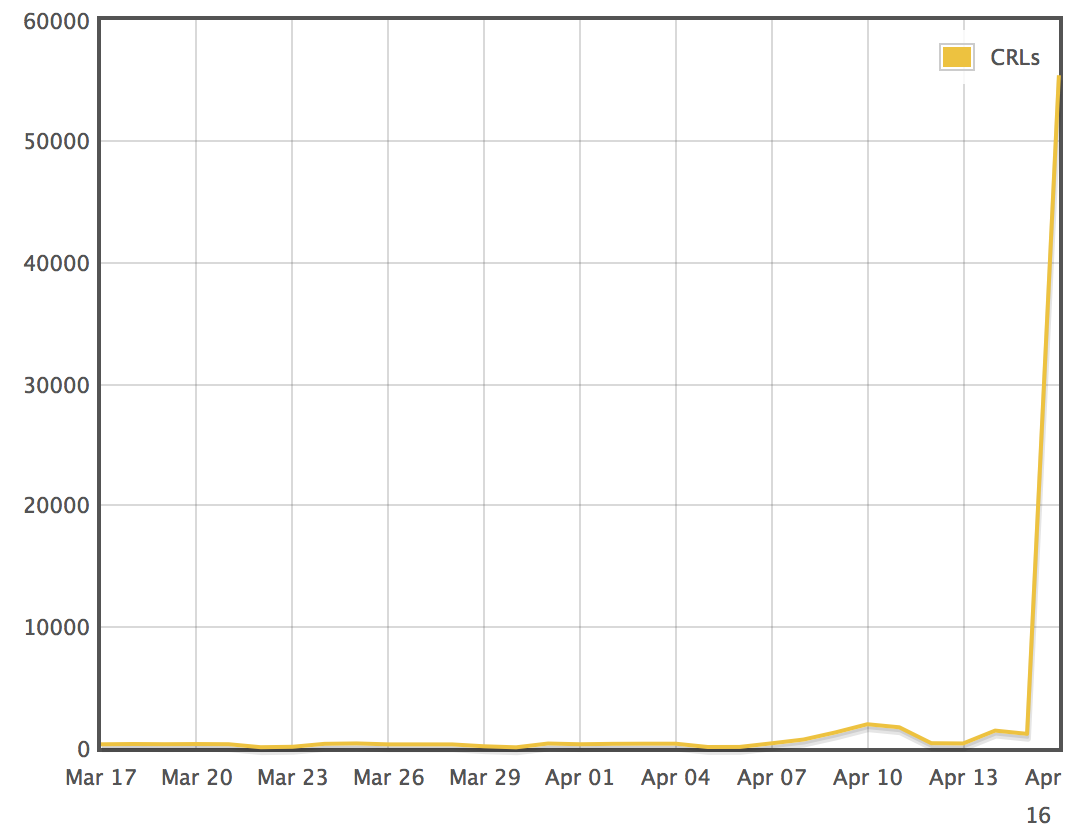
This is by an order of magnitude the largest spike in revocation activity seen in years, according to our current data.
I have set up a new page for everyone to monitor the activity as well as see how we are obtaining this data. The page can be found at https://isc.sans.edu/crls.html.
How will you use this page in your projects or general analysis? We'd love to hear some ideas.
If you know of other CRLs that we can add, please let us know in the comments! Additionally, if you would like to see an API call added so that you can automatically query us for this information, please let us know so that we are aware of the demand.
On a side note, we can see a clear upward trend in revocations over the past 3 or 4 years:
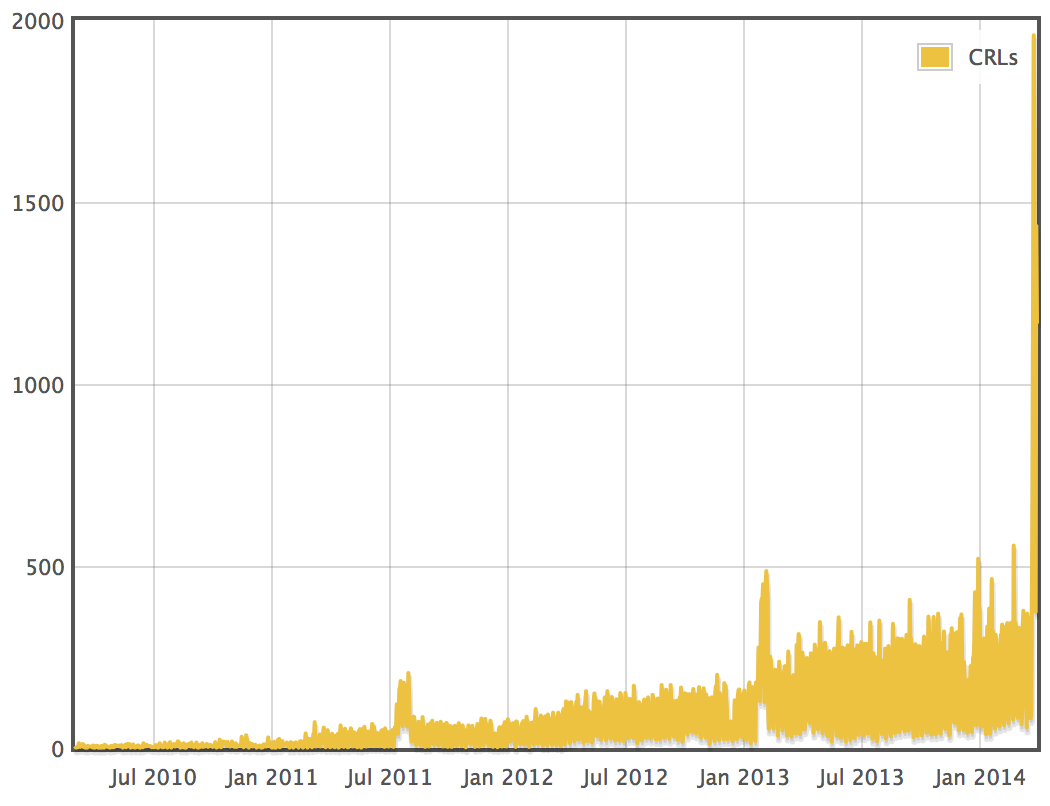
What do you attribute this consistent growth in revocations to? What do you think caused the previous spikes?
--
Alex Stanford - GIAC GWEB,
Research Operations Manager,
SANS Internet Storm Center
/in/alexstanford | @alexstanford
WinXP and/or Win2003 hanged systems because of SC Forefront Endpoint Protection faulty update
by Manuel Humberto Santander Pelaez (Version: 1)
Reader Philipp reported today a bug affecting his remaining Windows XP machines and Windows 2003 servers. Seems to be that all Windows XP and Windows 2003 machines with SC Forefront Endpoint Protection definition update 1.171.1.0 and later are affected. You might want to test definition update 1.171.64.0, as we have received reports stating that it fixes the problem. However, we have not seen yet any official statement from Microsoft regarding this issue.
If you disable Forefront because it's not letting your machine work, please place other controls that minimize the associated risk. Otherwise, your computers could be so easily hacked.
We also receive questions on which AV is the best. Since the answer is it depends on the company and the information security assets, you might want to check the Magic Quadrant for Endpoint Protection from Gartner Group and try to find yourself what is the best answer for your company. If you want to read the entire file, you can have it from Mcafee or Computerlinks.
We will update this diary if more information becomes available.
More information available at:
- http://msmvps.com/blogs/kenlin/archive/2014/04/16/winxp-and-or-win2003-with-sc-forefront-endpoint-protection-installed-msmpeng-exe-crashes-after-definition-update.aspx
- http://social.technet.microsoft.com/Forums/forefront/en-US/08cdcadc-5d7c-48c5-95d5-6e47291ddef0/scep-2012-432150-with-sigs-117110-causes-xp-to-hang-until-msmpeng-finally-crashes?forum=FCSNext
Manuel Humberto Santander Pelaez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org
Oracle Critical Patch Update for April 2014
Oracle released its quarterly Criticical Patch Update (CPU) yesterday [1]. As usual, the number of patches is quite intimidating. But remember these 104 fixes apply across the entire Oracle product range.
Some of the highlights:
CVE-2014-2406: A bug in Oracle's Database which allows a remotely authenticated user to gain control over the database.
37 new patches for Java SE, 35 of which allow remote execution as the user running the Java Applet (according to Oracle: "The CVSS scores below assume that a user running a Java applet or Java Web Start application has administrator privileges (typical on Windows)".
4 of the Java vulnerabilities have a base CVSS score of 10 indicating not only full remote code execution but also easy exploitability.
[1] http://www.oracle.com/technetwork/topics/security/cpuapr2014-1972952.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter


Comments