WhatsApp Malware Spam uses Geolocation to Mass Customize Filename
Malicious e-mails usually fall into two groups: Mass-mailed generic e-mails, and highly customized spear phishing attempts. In between these two groups fall e-mails that obviously do more to "mass customize" the e-mail based on information retrieved from other sources. E-mails that appear to come from your Facebook friends, or malware that harvests other social networks like Linkedin to craft a more personalized message.
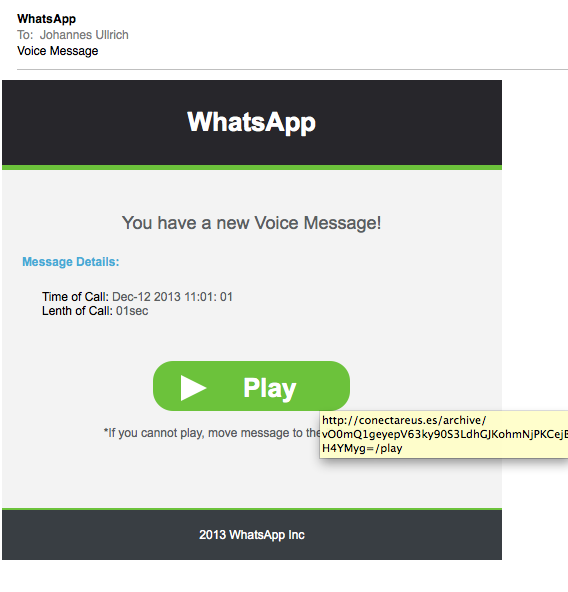
Today, I received one e-mail that I think was done pretty well and falls into the third category. The sender went through the trouble to craft a decent personalized message, trying to make me install some Spyware.
In this example, the e-mail advised me of a new "WhatsApp" message that may be waiting for me. The e-mail looks legit, and even the link is formed to make it look like a voicemail link with the little "/play" ending
(click on image to see larger version)
the part that I thought was the most interesting was the executable you are offered as you download the emails. The downloaded file is a ZIP file, and the file name of the included executable is adjusted to show a phone number that matches the location of the IP address from which the e-mail is downloaded from.
Downloading the message from my home in Jacksonville, I get: VoiceMail_Jacksonville_(904)458abcd.exe . On the other hand, downloading it from a server whose IP's geolocation commonly shows up in Wayne PA , the file name changes to VoiceMail_Wayne_(610)458abcd.exe. I obfuscated the last four digits of the phone number, but the last four digits appear random.
As usualy, anti-malware coverage is bad according to Virustotal [1]. Anubis doesn't show much interesting stuff here, but I wouldn't be surprised if the malware detected that it ran in an analysis environment [2]. Interestingly, it appears to pop up Notepad with a generic error message.
[1] https://www.virustotal.com/en/file/39457d452107fc019d0ece92d7a5c0c8d00ac5bf8dc3bd2411b0ad90cbcae194/analysis/1387029444/
[2] http://anubis.iseclab.org/?action=result&task_id=15eb462c46d9b95f4ed4d2750b1a52b0a
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter


Comments