Cyber Security Awareness Month - Day 5: Standards Body Soup, So many Flavors in the bowl.
Introduction
First I would like to say, without our readers and subscribers we would not exist and that we genuinely do read every post. A reader posted a request to break down standards bodies and I decided to take that endeavor on. This now has turned into a larger project than just one diary entry. You will see more on this topic but hopefully today is a good start. This first pass at understanding the different bodies does not include a complete list.
Many of likely heard the quote “The problem with Standards is there are so many to choose from.” I really don’t know who first uttered that phrase UPDATE: Andrew S. Tanenbaum [3] but it holds true from my point of view. This article will take a 10,000 meter or 30,000 foot view (Depends on if you are metric [1] or imperial Units [2] ) of what I am calling standards body soup. Within this bowl of standards groups there are several types and methods in which they govern. I can make the assumption that most of the readers are familiar with a Request for Comments (RFC) and the group that governs this standards suite is the Internet Engineering Task Force (IETF). So, we will start there and will break down the IEFT into areas for understanding. This will provide a framework for a further list of Standards Bodies.
Breakdown and Terminology
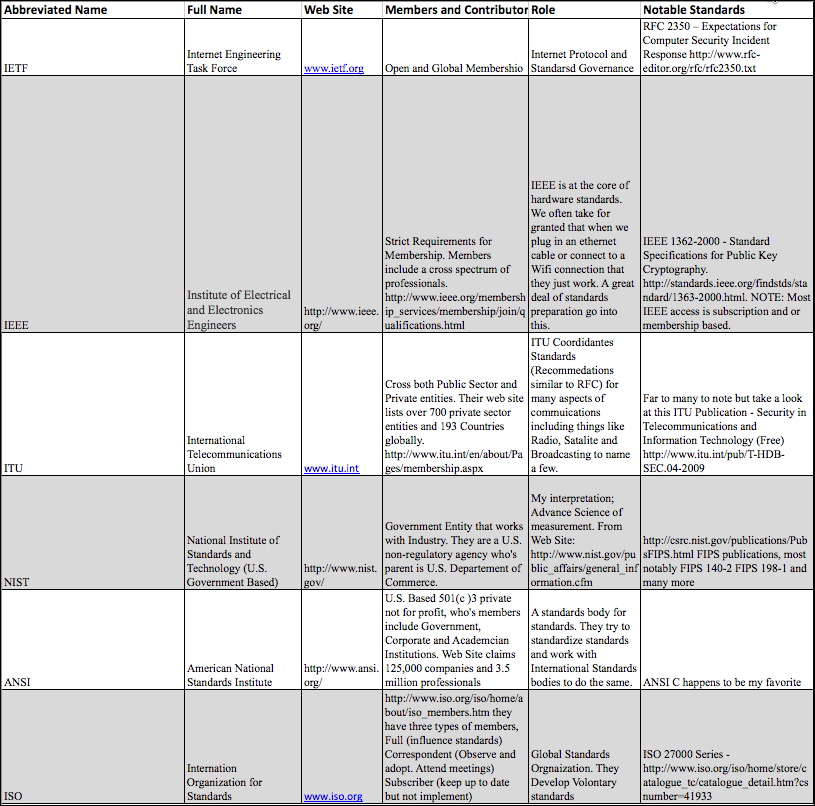
In order to build a table for understanding different standards bodies we will use the following subject areas for columns
Abbreviated Name: The short name or acronym used to reference the organization.
Full Name: The complete name. Sometimes we only know the Acronym.
Web Site: How to find them on the web.
Members and Contributors: Who can and or are members of the standards group.
Role: How do they influence or contribute to industry.
Notable Standards: Standards that might matter to us.
Standards Body Profile
Abbreviated Name: IETF
Full Name: Internet Engineering Task Force
Web Site: www.ietf.org
Members and Contributors: To Numerous to list. Membership is open to anyone and IETF is comprised of many working groups. A breakdown of working groups can be found at http://www.ietf.org/wg/ but in summary they are open to anyone and usually conduct business over open mailing lists. If there is an RFC that you would like to impact, join the mailing list and begin your journey.
The IETF Is governed by a group called the Internet Society (ISOC) and the board of trusties can be found at http://www.internetsociety.org/who-we-are/board-trustees. With most standards bodies, in our experience, the members are made up from various places. Members will often have a second industry position and their parent company allows them to contribute.
Role: Internet Standards Governance
Notable Security Based Standards: Again there are far too many notable standards to list from IETF but I will list a couple of my favorites.
RFC 2350 – Expectations for Computer Security Incident Response
http://www.rfc-editor.org/rfc/rfc2350.txt
On occasion we are asked things like “My Company/Group/Team/Org is looking to stand up an Incident Response Team, where do I start?” and in the spirit of the world we live in today I am re-coining a popular phrase to “There’s a Standard for that!”
RFC 4949 – Internet Security Glossary, Version 2
http://www.rfc-editor.org/rfc/rfc4949.txt
In case you were wondering, yes there are standards for the standards. This is an informational RFC, which means it is not really a standard but a good reference.
RFC 6618 (Experimental) – Mobile IPv6 Security Framework Using Transport Layer Security for Communication between the Mobile Node and Home Agent
http://datatracker.ietf.org/doc/rfc6618/
The title alone is scary but signs of a mobile world to come. This one is on my watch list.
Table
Please See Spreadsheet for editable details: https://isc.sans.edu/diaryimages/Standards_Framework_Draft.xlsx
(click on image for larger view)
Reports of a Distributed Injection Scan
We have received a report of a large distributed SQL Injection Scan from a reader. Behavior of scan is being reported as 9000+ Unique IPv4 Addresses and sends 4-10 requests to lightly fuzz the form field. Then the next IP will lightly fuzz the second form field within the same page and the next IP the next form field. Looks to be targeting MSSQL and seeking version.
The reader reports that this scan has been going on for several days.
Sample Payload:
%27%29%29%2F%2A%2A%2For%2F%2A%2A%2F1%3D%40%40version--
%27%2F%2A%2A%2For%2F%2A%2A%2F1%3D%40%40version--
%27%2F%2A%2A%2For%2F%2A%2A%2F1%3D%40%40version%29%29-
%29%29%2F%2A%2A%2For%2F%2A%2A%2F1%3D%40%40version--
%29%2F%2A%2A%2For%2F%2A%2A%2F1%3D%40%40version--
The User Agent String for all of the attacking IPs is always
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)
There does not seem to be a referrer page either.
If you are seeing this activity and can report it please let us know.
Richard Porter
--- ISC Handler on Duty
ISC Feature of the Week: Report Fake Tech Support Call Statistics
Overview
We previously featured our collection of Fake Tech Support Calls project. This scam is continuing and we are hearing more and more about these calls from both knowledgeable and unsuspecting users with varying levels of success or failure depending on your viewpoint.
This week we feature the initial statistical reporting on the data we collected so far at https://isc.sans.edu/reportfakecallstats.html!
Features
Overview - https://isc.sans.edu/reportfakecallstats.html#overview
Summary of project with privacy notice, link to submission form and soon-to-come API
Summary Table - https://isc.sans.edu/reportfakecallstats.html#summary
- Total number of submissions collected
- Total number of days collected on
- Average number of submissions per day
Summary of Fields - https://isc.sans.edu/reportfakecallstats.html#fields
Certain fields are multiple choice so we could pull some quick stats on them
More reporting and an API coming soon so stay tuned!
Related diaries:
https://isc.sans.edu/diary/Fake+tech+reps+calling/12874 by Daniel Wesemann
https://isc.sans.edu/diary/Fake+Support+Calls+Reported/14215 by Kevin Shortt
Related podcasts:
https://isc.sans.edu/podcastdetail.html?id=2848 - by Johannes Ullrich
https://isc.sans.edu/podcastdetail.html?id=2539 by Johannes Ullrich
Post suggestions or comments in the section below or send us any questions or comments in the contact form on https://isc.sans.edu/contact.html#contact-form
--
Adam Swanger, Web Developer (GWEB, GWAPT)
Internet Storm Center https://isc.sans.edu


Comments