VMware releases updates - don't forget to patch
An ISC reader notified us that VMware released updates for for ACE, Server, Player and Workstation products:
According to VMware, the following 3 security issues are patched by the updates for VMware ACE, Player and Workstation:
- Setting ActiveX killbit. "VMware has set the killbit on its ActiveX controls. Setting the killbit ensures that ActiveX controls cannot run in Internet Explorer (IE), and avoids security issues involving ActiveX controls in IE."
- Update to FreeType. "FreeType 2.3.6 resolves an integer overflow vulnerability and other vulnerabilities that can allow malicious users to run arbitrary code or might cause a denial-of-service after reading a maliciously crafted file."
- Update to Cairo. "Cairo 1.4.12 resolves an integer overflow vulnerability that can allow malicious users to run arbitrary code or might cause a denial-of-service after reading a maliciously crafted PNG file."
The following 4 security issues are patched by the updates for VMware Server:
- Security Fix for VMware ISAPI Extension. "One of the ISAPI extensions provided by VMware is vulnerable to a remote denial of service. "
- Security Fix for Local Privilege Escalation on Host System. "Exploitation of this vulnerability allows users to run arbitrary code on the host system with elevated privileges."
- Update to Freetype. "FreeType 2.3.6 resolves an integer overflow vulnerability and other vulnerabilities that can allow malicious users to run arbitrary code or might cause a denial-of-service after reading a maliciously crafted file."
- Setting ActiveX killbit. "VMware has set the killbit on its ActiveX controls. Setting the killbit ensures that ActiveX controls cannot run in Internet Explorer (IE), and avoids security issues involving ActiveX controls in IE."
Patching VMware is never a pleasant experience, and usually involves a heavy download and a lengthy installation, not to mention the testing to ensure your environment is not adversely affected by the patch. What's a better way to spend your weekend?
Update: (2008-08-30-15:50 UTC) The VMware bulletin can be found at http://lists.vmware.com/pipermail/security-announce/2008/000033.html
-- Lenny
Lenny Zeltser leads a regional security consulting team at Savvis and teaches a course on reverse-engineering malware at SANS.
Scammers may use recorded snippets during voice phishing
The vishing (voice phishing) incident described in an earlier diary seemed to use a rudimentary voice synthesizer to request information from the caller. An ISC reader noted that in more sophisticated attacks, scammers employ "sampling"--recorded snippets of actual calls to sound more legitimate.
He submitted the following outline of the call he received the other day:
"XXX Bank values your business, please hold for next representative."
Hold music plays...
"Call being transferred to automated information system."
The above seemed to be recorded sound files from an actual call to the bank, as this is exactly what you would hear if you called the bank and chose to use their automated system.
"You have been selected to receive a special offer from XXX Bank. For a limited time you can receive 0% interest for 6 months on existing balances on your XXX Bank card. You can apply over the phone or online at www dot XXX Bank dot com. Press 1 to apply now."
You press 1 (or any number).
"To apply for the offer please enter your credit card now" (Computer generated voice)
You enter the card number.
"Please enter your PIN number now."
You enter the PIN.
"Thank you, processing account information now." (Again, a recorded snippet from the real bank's voice system.)
"Your request has been processed and will appear on your next account statement, goodbye." (wav file sampled from banks real voice mail system.)
The ISC reader pointed out that this call highlights the following evolution in the scammers' tactics:
- They had put effort into sampling real voice prompts from banks automated phone system.
- They gave out the bank's real web address, presumably to give an air of legitimacy to the call.
Thanks, ISC reader!
-- Lenny
Lenny Zeltser leads a regional security consulting team at Savvis and teaches a course on reverse-engineering malware at SANS.
Scams from today's mailbag
Here are a few scam-related messages we received in the inbox today. A common thread is that the scammers keep thinking creatively about lowering the recepient's guard:
- In the first example is a VoIP-based phishing (vishing) attack, where the scammer exploits people's tendency to trust the phone more than email.
- In the next example, the scammer avoids asking for or promising money directly, so as not to arouse suspicions prematurely.
- In the last example, the scammer acknowledges the dangers of scams, and claims to offer support to people who fell victim to them.
VoIP Phishing
Mike sent us a copy of a message that claimed to come from the City Credit Union, and asked the recipient to call a particular number because the recipient's account was temporarily suspended:
From: City Credit Union [mailto:do-not-reply@citycu.org]
Date: Friday, August 29, 2008
Subject: PLEASE CALL US! Account Temporary Suspended !Dear Customer,
On August 28 14:28:34 EST 2008 you or someone changed your online password on City Credit Union website.
For security reasons, your account was temporary suspended.
If this request was not performed by you please log in and solve the problem.
To continue please call us at:
(214) 431-4XXX
We replace the last 3 digits with XXX, just in case. According to Mike, when you call, "you get a very old style computer voice asking you to input your debit credit card number." Mike is a customer of City Credit Union.
A very similar scam was reported by the Blog of Scams a few days ago--very similar text, but it referred to APL Federal Credit Union instead. For additional examples of vishing, see an earlier diary.
Baiting the Victim
In the next and unrelated example today's mailbag, we encounter a dying widow looking of an arms dealer, looking to make friends on the Internet:
From: Hilary Whitney [hilaryw.......@gmail....]
Date: Friday, August 29, 2008
Subject: Good dayBeside India House
Aldwvch London WC2B 4NA.
Email; mrsshilarywhitney@yahoo.co.uk
Good dayAm glad to have the opportunity to contact you with the labtop the nurse brings for me. ...
I am married to late Mr Cosmos Whitney,a licensed arms dealer and a soldier before he died in the year 1998. ... Presently,my doctor told me that i would not last for the next 30 days due to a rare form of cancer of the pancress. ...
Presently,my doctor told me that i would not last for the next 30 days due to a rare form of cancer of the pancress. ... i hoped to find a good person whom i can find trust worthy to stand as a good friend since i don't have any relatives,friends and children's as well.And also since i have limited time to live.
I want to know if your a honest and caring person,because am not used to internet friends.
Notice that the message implies that the sender is wealthy, and without anyone to receive inheritance when she passes away. This detail is meant to bait the recipient, who might hope to get the money after befriending Mrs. Hilary Whitney. While this message was submitted via email, a version of it was also distributed via blog spam as early as May 23, 2008.
Scammers Against Scams
Our last example seems to be an outreach email for helping victims of Nigerian-style scams. In reality, it is an attempt to gain the recipients' trust to defraud them. The technique is similar to the example we described in an earlier diary.
From: "Brian Adams" <baantinigeriascams@gmail.com>
Date: Sat, 23 Aug 2008
Subject: Anti Nigeria Scams Ref: 23524326
Attention:This email is not in any manner directed to you, but its purposely and specifically directed to Nigeria Scam victims. . However, if you have fallen for Nigerian Scams, do not hesitate to contact us or visit our website for more details on how we can help.
We shall be waiting to hearing from you been certain that you were truly scammed by a Nigerian and you have proves to back your claims. Please read the full report at our website:
http://www.nigeria-scamvictims.itgo.com/Yours faithfully,
Brian Adams
Nigerian Government Reimbursement Committee
Several instances of this scam were observed on the web recently (see 1, 2), and a Google search for "Nigerian Government Reimbursement Committee" shows numerous hits that suggest fraudulent activities.
-- Lenny
Lenny Zeltser leads a regional security consulting team at Savvis and teaches a course on reverse-engineering malware at SANS.
SWOT matrix for describing security posture
"Be brief, for no discourse can please when too long." Miguel de Cervantes
"When I try to be brief, I become obscure." Quintus Horatius Flaccus
How can you outline a system's security state succinctly, yet without omitting important points? Consider using the SWOT matrix to summarize your perspective. This approach is particularly effective when communicating with managers and executives, who are usually familiar with SWOT analysis.
The acronym SWOT, which stands for Strengths, Weaknesses, Opportunities and Threats, is designed to remind you of the key factors to consider when analyzing a situation. A SWOT matrix is a table that presents these elements in a compact manner. Take a look the SWOT matrix template below. (It is based on an image from Wikipedia.)
The left column lists helpful, positive factors; the right one lists harmful, negative factors. The top row includes the factors intrinsic to the analyzed system; the bottom one includes factors external to the system.
Let's examine contents of each cell in the SWOT matrix: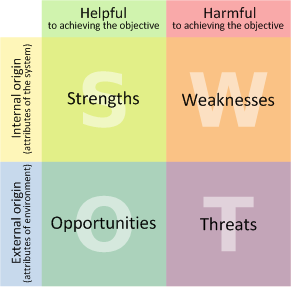
Strengths lists the most effective security aspects of the system, for example tight network access controls or comprehensive security policies. Improvements to the system's security can be accomplished by building upon these strengths.
Weaknesses outlines those aspects of the system that put it at risk, for instance poor input validation, or lack of effective log management. These aspects of the system should be improved.
Opportunities describes factors external to the system that can help improve its security. This might be the availability of security training funds for developers, or the existence of a logging system that has been purchased, but was never deployed. Items in this cell might be low-hanging-fruit--easy wins that can improve the system's security.
Threats highlights external factors that magnify the adverse effects of internal system weaknesses. For instance, the company may be subject to fine-imposing regulations, or may possess weak change management practices.
The SWOT matrix approach is particularly powerful when the company defines the objective with respect to which the system should be evaluated. In the context of information security, this usually involves agreeing on the system's risk profile, data sensitivity, business goals, and other factors that affect the system's security architecture.
If you like this approach, you are welcome to use the editable SWOT matrix template I created in Microsoft Word. You can download it from here.
Further information: For information about the classic use of SWOT analysis, take a look at the corresponding Wikipedia article. Security management topics such as SWOT analysis are explored in the SANS MGT-512 course. If you found this note useful, you may also enjoy my earlier tip on using an "elevator pitch" for explaining security risks to executives.
-- Lenny
Lenny Zeltser leads a regional security consulting team at Savvis and teaches a course on reverse-engineering malware at SANS.


Comments